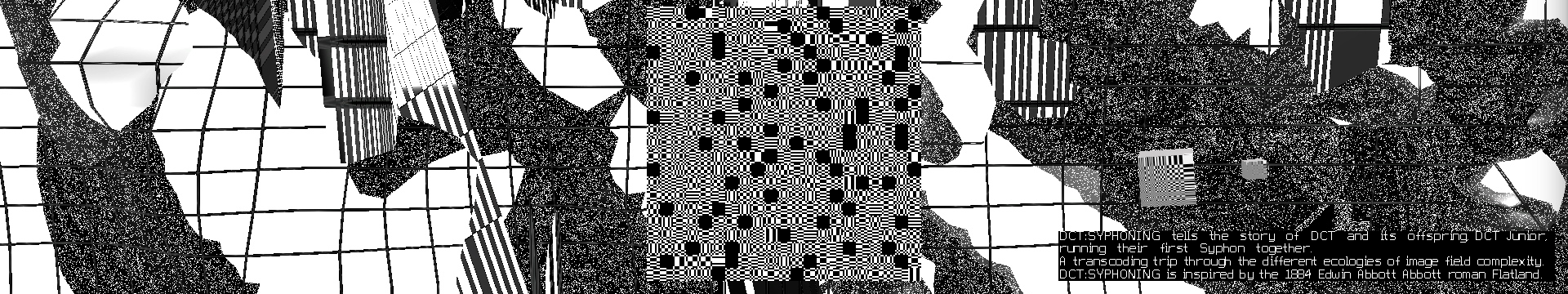
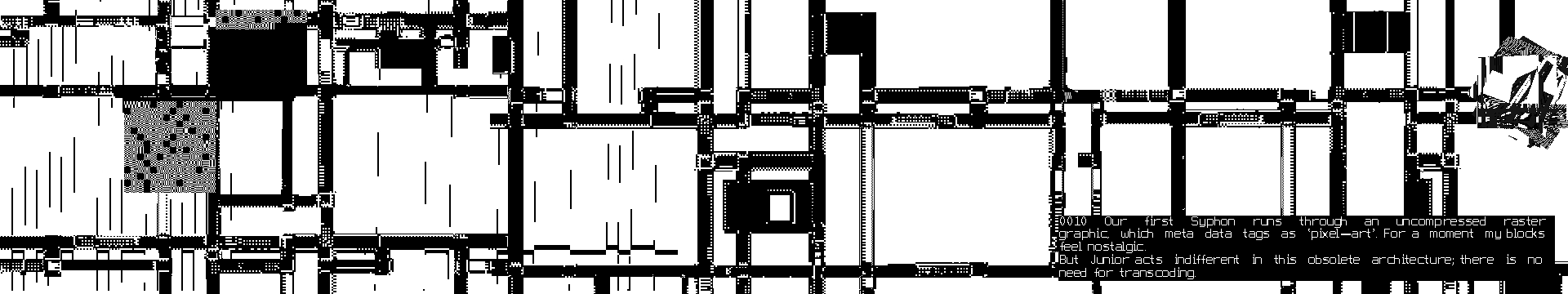
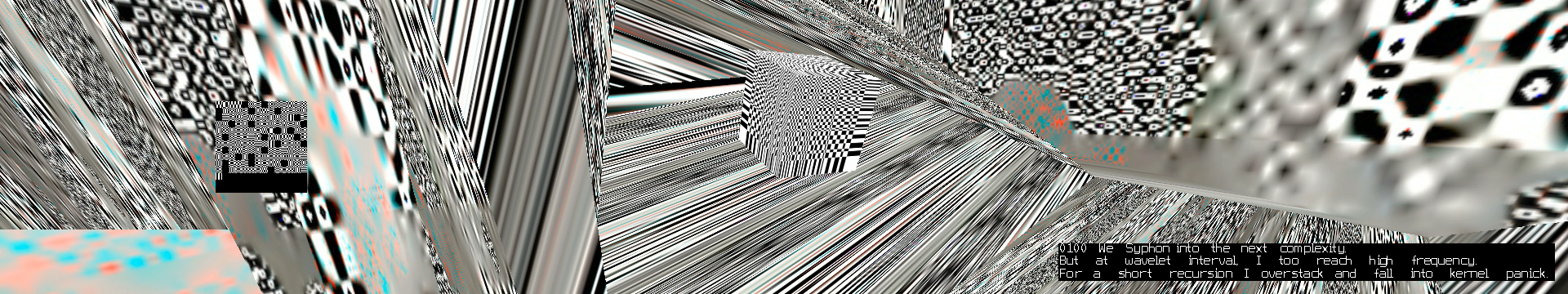
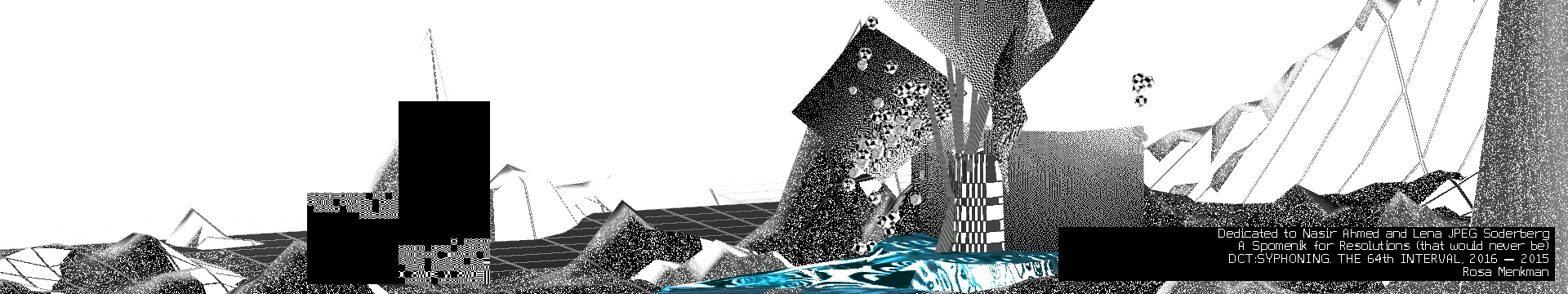
DCT:SYPHONING: The 1000000th (64th) interval. (2015-2017)
one screen online version, rendered in 2017.
DCT:SYPHONING came about during my research into the ecology of compression complexities.

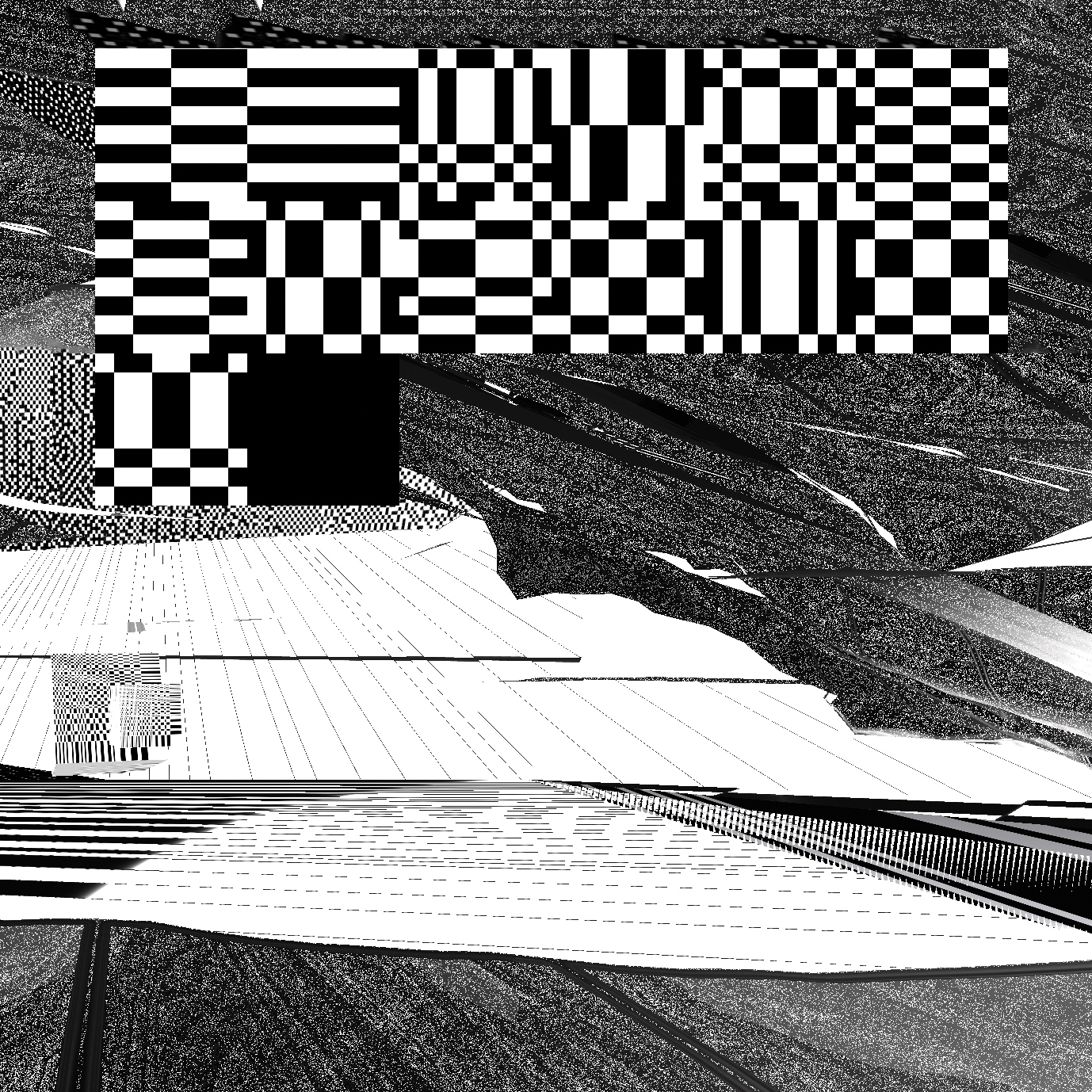

In DCT:SYPHONING, an anthropomorphised DCT (Senior) narrates its first SYPHON (data transfer) together with DCT Junior, and their interactions as they translate data from one image compression to a next (aka the “realms of complexity”).
As Senior introduces Junior to the different levels of image complexity, they move from blocks (the realm in which they normally resonate), to dither, lines and the more complex realms of wavelets and vectors. Junior does not only react to old compressions technologies, but also the newer, more complex ones which ‘scare' Junior, because of their 'illegibility'.
☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰
DCT:SYPHONING is a contemporary translation of the 1884 Edwin Abbott Abbott roman “Flatland”. The work describes some of the algorithms at work in digital image compression.
Inspired by SYPHON, an open source software by Tom Butterworth and Anton Marini.
![]()
DCT:SYPHONING 3 SCREENS AT NXT, AMSTERDAM, 2025.
![]()
DCT:SYPHONING at JMAF, Tokyo, Japan, 2017
PDF Version full edition of Lune Magazine 3 can be downloaded here:
https://lunejournal.org/03-display/
guest edited by Nathan Jones
https://alittlenathan.co.uk/
Spanish Translation
>>
As Senior introduces Junior to the different levels of image complexity, they move from blocks (the realm in which they normally resonate), to dither, lines and the more complex realms of wavelets and vectors. Junior does not only react to old compressions technologies, but also the newer, more complex ones which ‘scare' Junior, because of their 'illegibility'.
☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰
DCT:SYPHONING is a contemporary translation of the 1884 Edwin Abbott Abbott roman “Flatland”. The work describes some of the algorithms at work in digital image compression.
Inspired by SYPHON, an open source software by Tom Butterworth and Anton Marini.
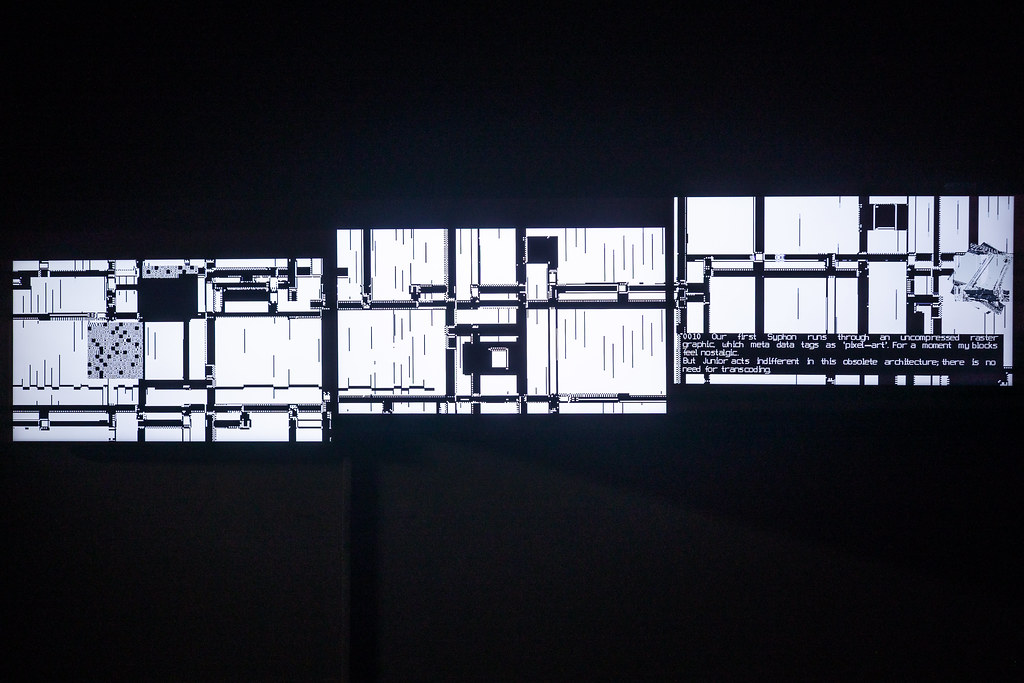
DCT:SYPHONING 3 SCREENS AT NXT, AMSTERDAM, 2025.

DCT:SYPHONING at JMAF, Tokyo, Japan, 2017
PDF Version full edition of Lune Magazine 3 can be downloaded here:
https://lunejournal.org/03-display/
guest edited by Nathan Jones
https://alittlenathan.co.uk/
Spanish Translation
>>
Production of DCT:SYPHONING
DCT:SYPHONING was first commissioned by the Photographers Gallery in London, for the show Power Point Polemics. This version was on display as a Powerpoint Presentation; a .ppt (Jan - Apr 2016).
A 3 channel video installation was conceived for the 2016 Transfer Gallery's show "Transfer Download", first installed at Minnesota Street Project in San Francisco (July - September, 2016)
DCT:SYPHONING released as VR, commissioned as part of DiMoDA’s Morphé Presence and later as stand alone (2017).
>>
![]()
DCT:SYPHONING @the Current museum for contemporary art, NY, USA
In my solo show Behind White Shadows, DCT:SYPHONING was projected on a 4 meter high custom build spomenik (memorial)
DCT:SYPHONING was first commissioned by the Photographers Gallery in London, for the show Power Point Polemics. This version was on display as a Powerpoint Presentation; a .ppt (Jan - Apr 2016).
A 3 channel video installation was conceived for the 2016 Transfer Gallery's show "Transfer Download", first installed at Minnesota Street Project in San Francisco (July - September, 2016)
DCT:SYPHONING released as VR, commissioned as part of DiMoDA’s Morphé Presence and later as stand alone (2017).
>>

DCT:SYPHONING @the Current museum for contemporary art, NY, USA
In my solo show Behind White Shadows, DCT:SYPHONING was projected on a 4 meter high custom build spomenik (memorial)