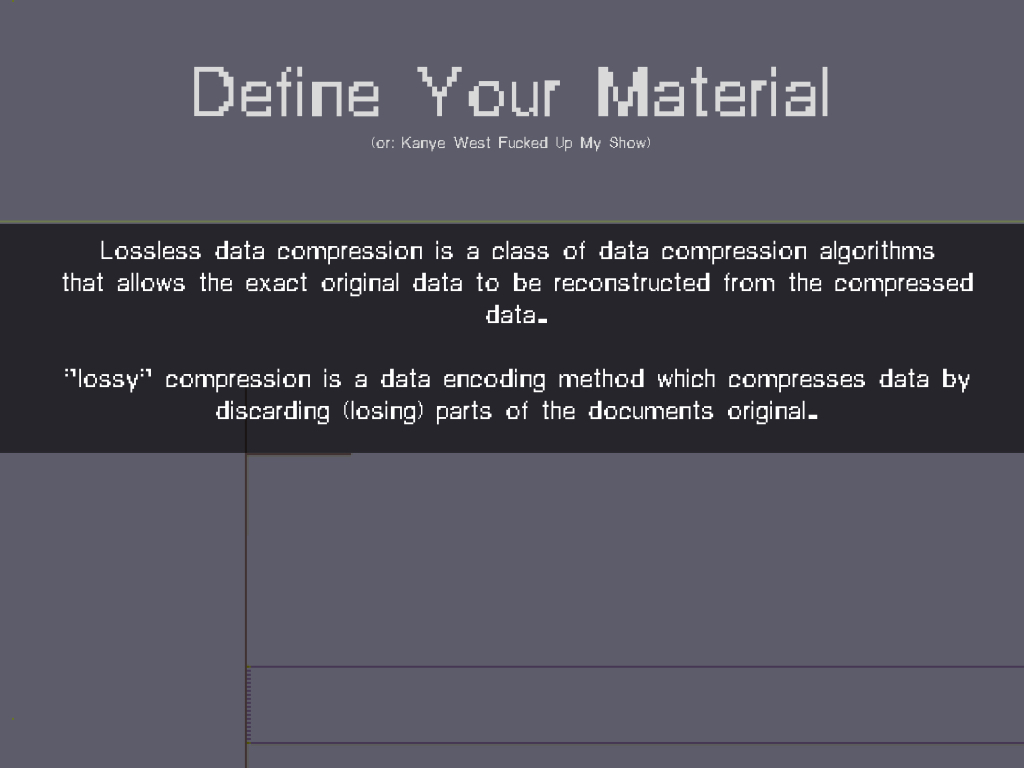
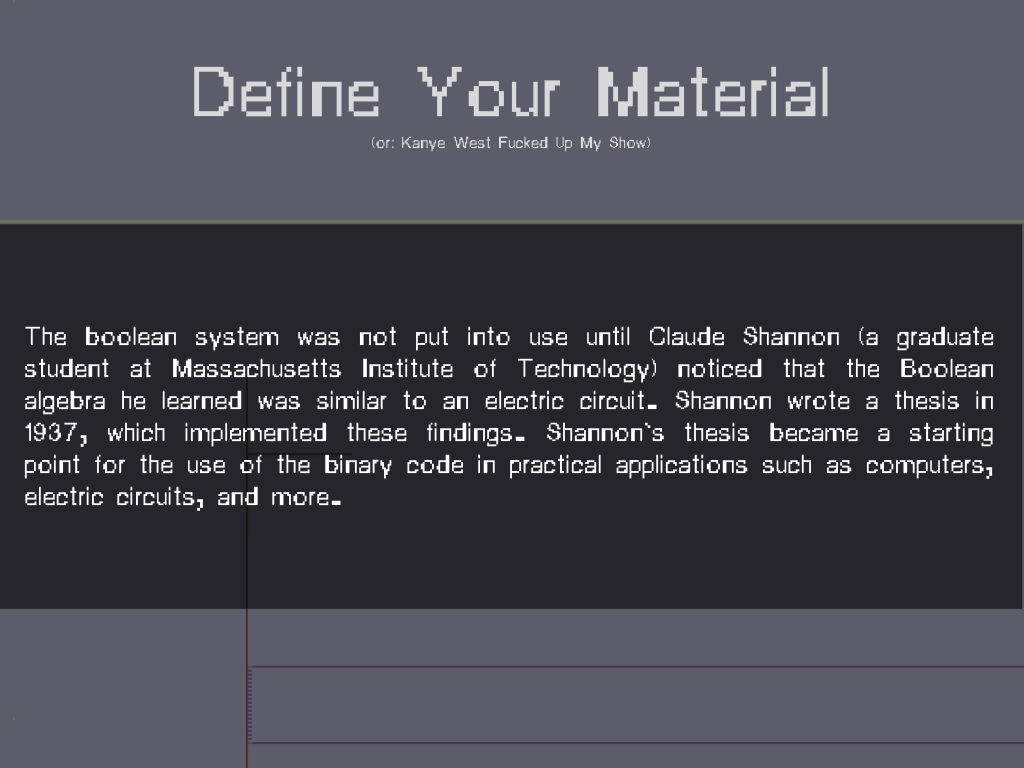
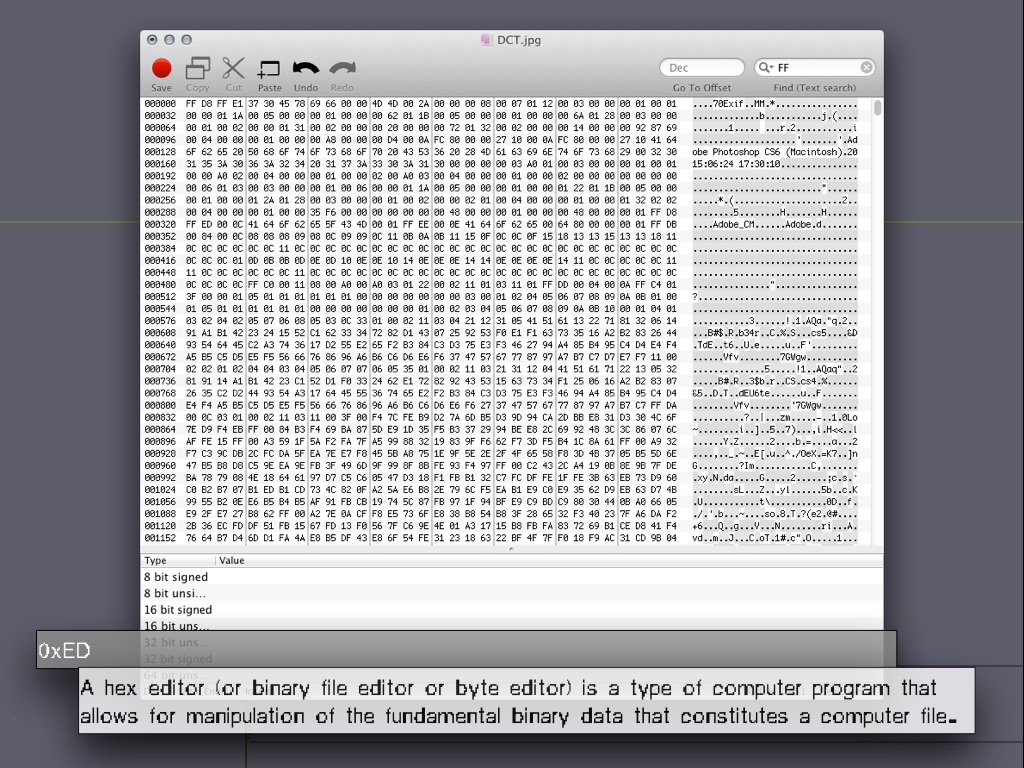
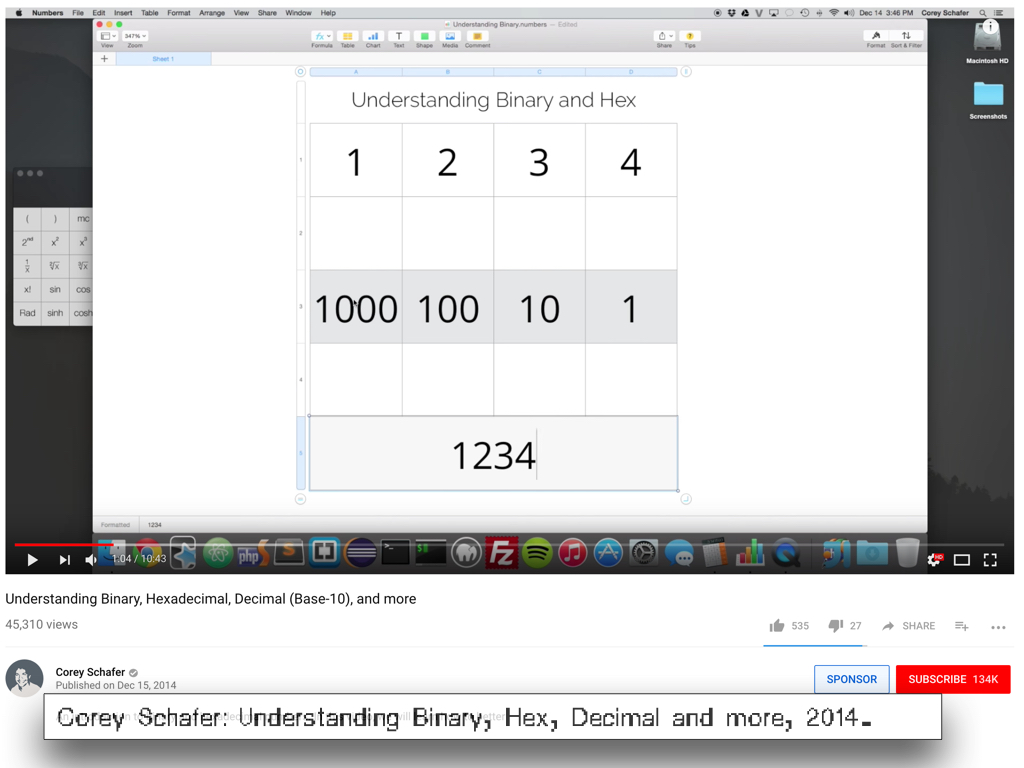
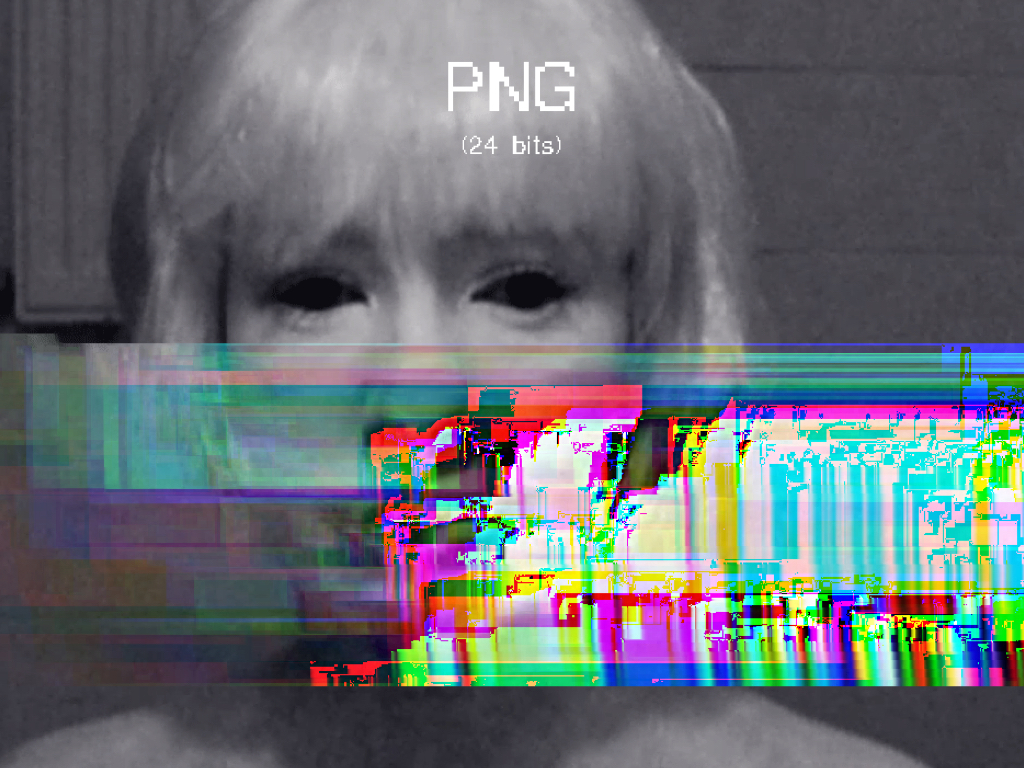MATERIAL: Bends and breaks, from Material Evidence to Material Index
Material, material specificity and materiality ---
WRITTEN (THEORY)
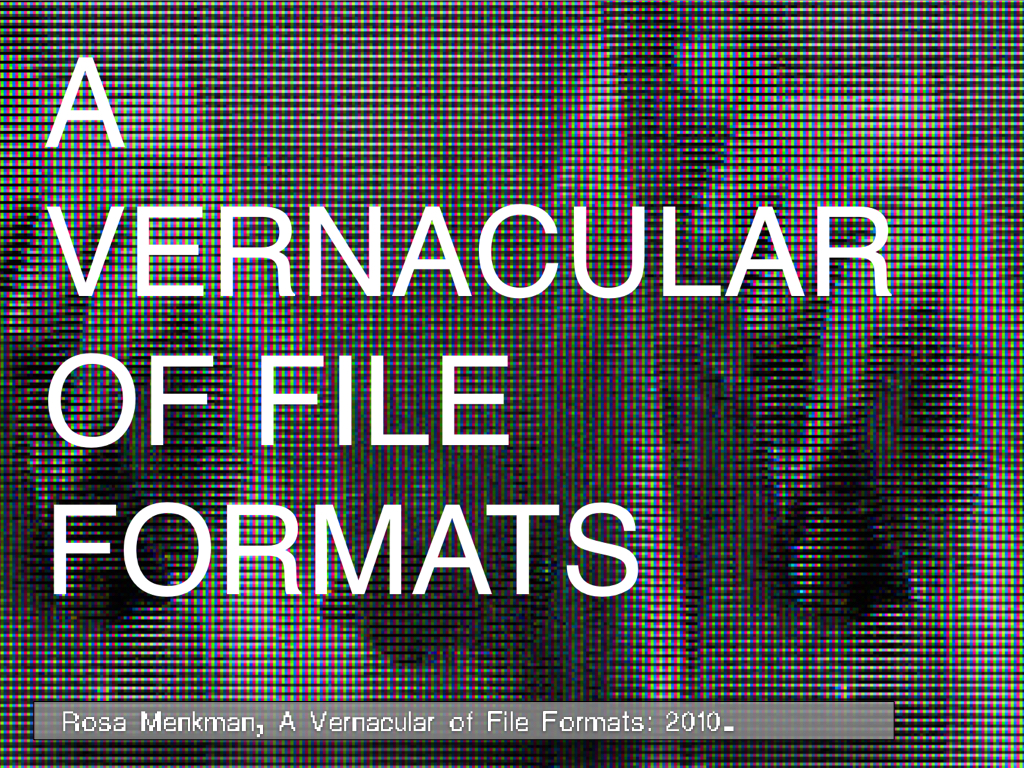
>>> Vernacular of File Formats [pdf] (2010 - ... )
>>> Sonification / Databending Workshop materials
>>>
ARTWORKS (PRACTICE)
>>> Videoscapes (2008 - ... )
>>> Un/Resolved (2020)
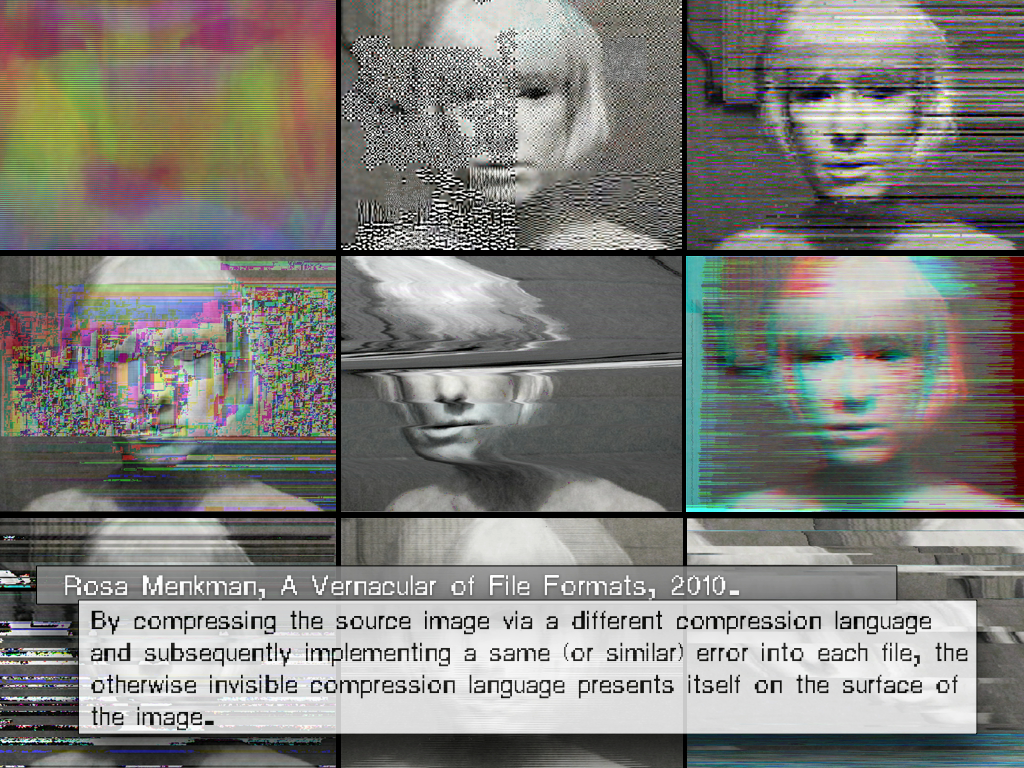
>>> Vernacular of File Formats (2010 - ... )
>>> Dear MR. Compression (2010)
>>> Monglot (glitch software) (2011)
>>> Extrafile vs Monglot (2011)
>>> Vernacular of File Formats [pdf] (2010 - ... )
>>> Sonification / Databending Workshop materials
>>>
ARTWORKS (PRACTICE)
>>> Videoscapes (2008 - ... )
>>> Un/Resolved (2020)
>>> Vernacular of File Formats (2010 - ... )
>>> Dear MR. Compression (2010)
>>> Monglot (glitch software) (2011)
>>> Extrafile vs Monglot (2011)
WRITTEN (THEORY)
ECOLOGY OF DCT MACROBLOCKS
>>> DCT: THE GUY BEHIND THE GUY BEHIND THE GUY (2015)
or: How Not to be Read (a recipe using Discrete Cosine Transform) [ pdf ]
ARTWORKS (PRACTICE)
>>> An Ecology of Compression Complexities (2017)
>>> DCT:SYPHONING. The 1000000th (64th) interval (2015 - 2017)
>>> DCT (CRYPTOGRAPHY) (2015)
>>> i.R.D. PATCH (with DCT key) (2015)
>>> JPEG (revision for Sotherby’s) (2023)
ECOLOGY OF DCT MACROBLOCKS
>>> DCT: THE GUY BEHIND THE GUY BEHIND THE GUY (2015)
or: How Not to be Read (a recipe using Discrete Cosine Transform) [ pdf ]
ARTWORKS (PRACTICE)
>>> An Ecology of Compression Complexities (2017)
>>> DCT:SYPHONING. The 1000000th (64th) interval (2015 - 2017)
>>> DCT (CRYPTOGRAPHY) (2015)
>>> i.R.D. PATCH (with DCT key) (2015)
>>> JPEG (revision for Sotherby’s) (2023)
- Schuppli, Susan. Dark Matters: an interview with Susan Schuppli, in: Living Earth, 2016.
“Materiality is reconceptualized as the interplay between a text's physical characteristics and its signifying strategies, a move that entwines instantiation and signification at the outset. This definition opens the possibility of considering texts as embodied entities while still maintaining a central focus on interpretation. It makes materiality an emergent property, so that it cannot be specified in advance, as if it were a pre-given entity. Rather, materiality is open to debate and interpretation, ensuring that discussions about the text's "meaning" will also take into account its physical specificity as well.”
- Hayles, N. Katherine. "Print is flat, code is deep: The importance of media-specific analysis." Poetics Today 25.1 (2004): 67-90.
A reflexive approach to materiality makes it possible to re-conceptualize materiality itself as ‘the interplay between a text’s physical characteristics and its signifying strategies’. Rather than thinking in the mediums’ material as fixed in physicality, a re-definition of materiality is useful because it opens the possibility of considering any text as embodied entity “while still maintaining a central focus on interpretation. In this view of materiality, it is not merely an inert collection of physical properties but a dynamic quality that emerges from the interplay between the text as a physical artifact, its conceptual content, and the interpretive activities of readers and writers.”
Reflections on materiality should not just happen on a technological level. To fully understand a work, each level of materiality should be studied: the physical and technological artifact, its conceptual content, and the interpretive activities of reader, artist and audience. [the choice of any] digital material is not innocent or meaningless. With enough knowledge of the material, an investigation into digital materialilty can uncover stories about the origin and history of the material, by others.
▁∣∖▁╱◝◟.❘╱▔▔╲̸/╲╱▔▔▔╲∣∖╱▔╲▁▁∣∖▁╱◝◟.╱▔▔╲________
How many efforts are required in order to watch?
Whenever I use a ‘normal’, transparent technology, I aim to see 'through' the actual machine. I have learned to unsee its interface and all its structural components. I am able to understand its message and use the technology as fast as possible. In a way I have learned to become blind to (certain parts of) technology.
Similar lines of development have taken place in my perception of sound. As Canadian composer R. Murray Schafer wrote: "We have no ear lids. We are condemned to listen. But this does not mean our ears are always open." Over the years I have learned to close my ear lids and even might have lost (or never developed) some of the sensitivities needed for 'deep listening' (or ‘deep watching’).
The quest to make the public re-hear certain sounds, to educate the listener and to 'open up ear lids', has been a subject pursued by many different sound artists. Acousmatics for instance, a strand of sound art developed by the French composer and pioneer of musique concrète Pierre Schaeffer, lets the audience listen to the sounds originating from behind a "black veil". The source or instrument of the sound remains unseen and unknown while the non-representational or formalist sound forces the audience to focus on active listening.
Has similar research and work been made in the visual arts? Does some form of acousmatic video or even acousmatic videoscapes exist? What would this look like and could glitch play a role in this?
While watching glitch art, the audience perceives glitches without (often) knowing how they came about, which gives them an opportunity to concentrate on their form - to interpret its structures and to learn more from what can actually be seen. In a sense many glitches follow the principle of acousmatics visually.
A videoscape should be a place where artists can create a new, visual ecology that can give playful feedback on the technological conventions that control the spectator in their everyday life. In these conceptually fueled videoscapes we can open our eyes for the unreasonable and give form to what we so often have tried to obfuscate in both audio and visual media, namely artifacts.
The main subject of most glitch art is 'critical perception'. Critical in this sense is twofold; either criticizing the way technology is conventionally perceived, or showing the medium in a critical state. Glitches release a critical potential that forces the viewer to actively reflect on the technology.
The acousmatic videoscape thus uses critical trans-media aesthetics to theorize the human thinking about technology; it creates an opportunity for self reflexivity, self critique and self expression.
The acousmatic videoscape is a space in which I can perceive output outside of my goggles of speed, transparency and usability. The new structures that unfold themselves can be interpreted as a portal to an utopia, a paradise like dimension, but also as a black hole that threatens to destroy the technology as I knew it. Here is a purgatory; an intermediate state between the death of the old technology and a judgement for a possible continuation into a new form of seeing and using, a new perspective…
︎ Videoscapes
 8448 x 4 CM
8448 x 4 CM long painting
on canvas,
or
data file
to be wrapped
on hardware

 8448 x 4 CM long painting on canvas, or data file,
8448 x 4 CM long painting on canvas, or data file, to be wrapped over hardware (a painting of 32 x 32 pixels wide, 1 pixel deep, both sides)
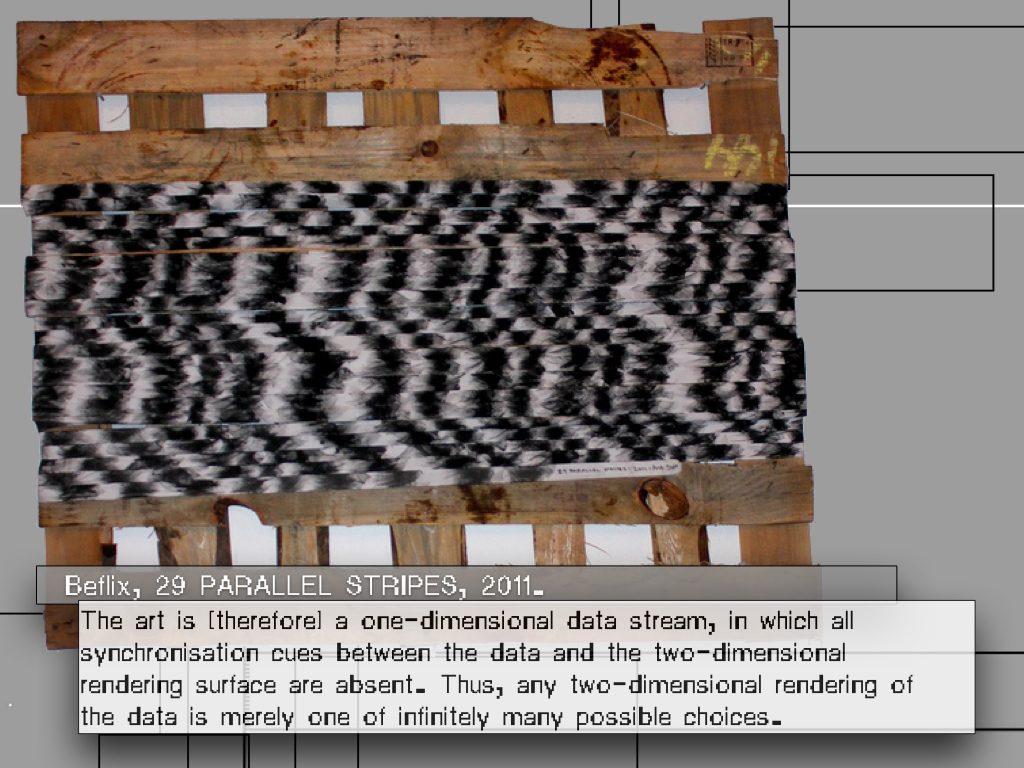
Inspired by the 2011 works “Beyond Yes and No” and “29 PARALLEL STRIPES”, by Beflix,
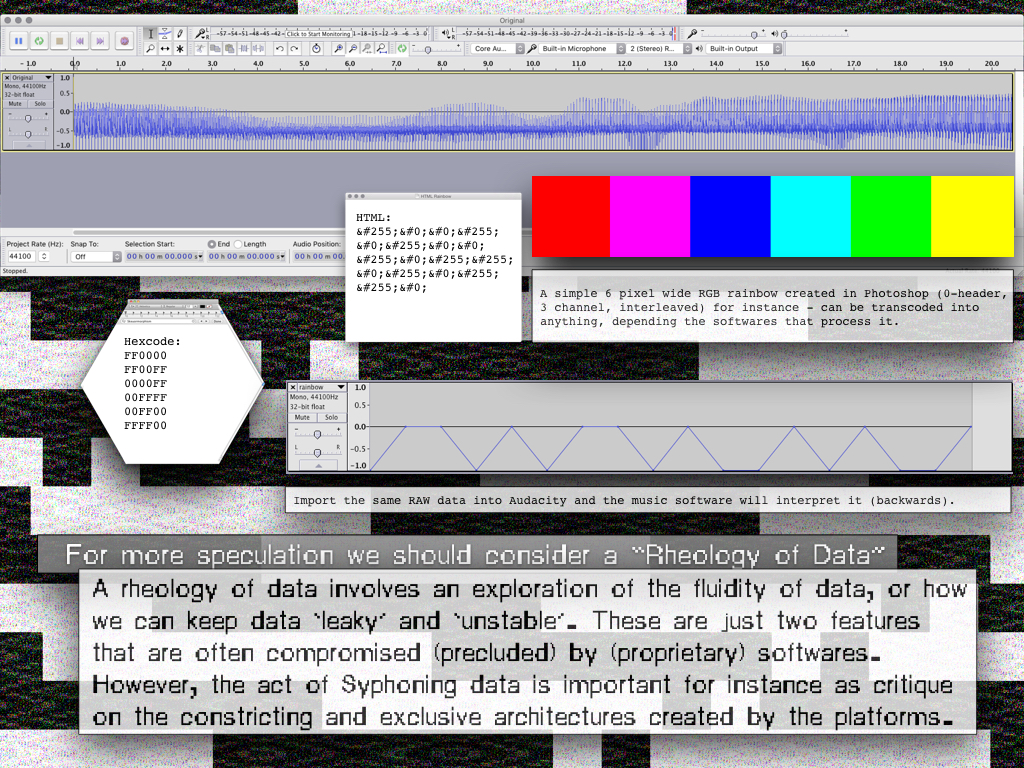
UnResolved explores the fluidity of data and illustrates how the transition from analogue to digital incorporates both vertical quantitative resolution (as seen in analogue systems like PAL, which is 576p) and horizontal resolution.
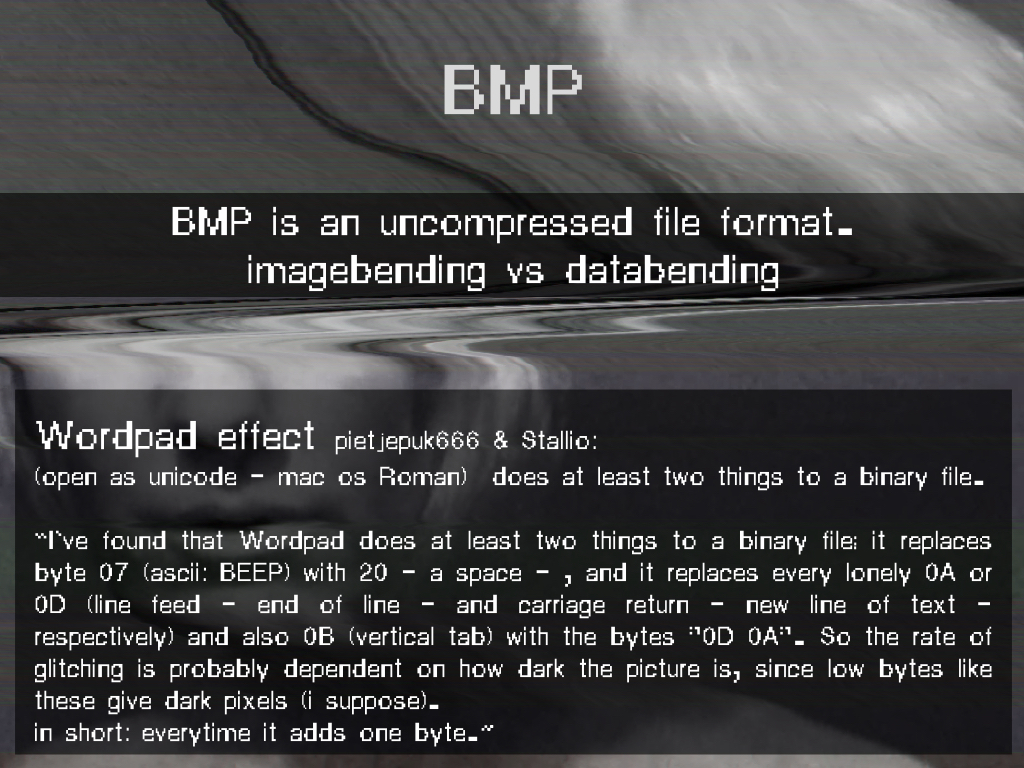
Using a bitmap image, I followed the linear organization of pixelated data. In a .BMP (raster image data file), the image's luminance and chrominance data are encoded pixel by pixel in a linear sequence, one after the other.
In UnResolved, every pixel or data point is hand-painted onto a 64-meter-long canvas strip, which is then mounted on a frame. When wrapped correctly and unrolled over hardware with the right dimensions, UnResolved reveals a double-sided image: one side shows my portrait, and the other side displays a cryptographic message in DCT (a cryptographic tool developed in 2015): BEYONDRESOLUTION.
With UnResolved I demonstrate how a bitmap file, when ‘opened’ on different hardware, can generate alternate modes of reading, writing or seeing:
the hardware defines what is perceived.

some images of the making of: 32 stripes of canvas were encoded, sewn into a very long strip, and painted.

PDF: A Guide to Databend Compression Design, 2010.
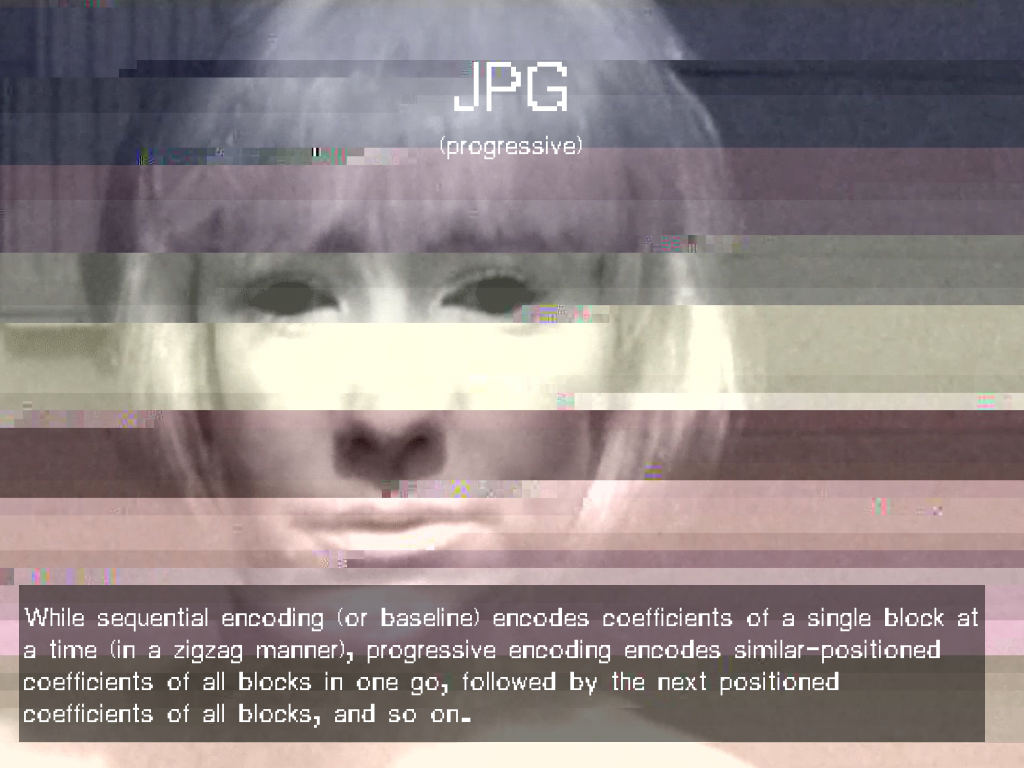
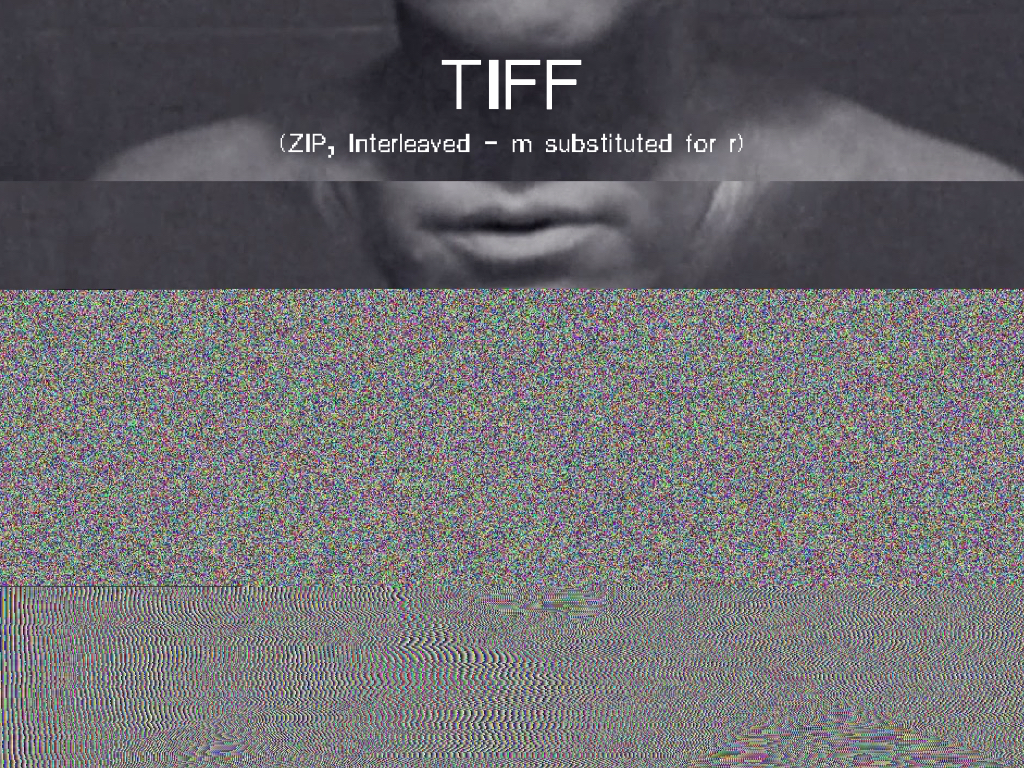
In A Vernacular of File Formats, I subsequently compressed a source image (a still of the Collapse of PAL featuring my face) via different compression languages. I then implemented a same (or similar) error into each file, to let the otherwise invisible compression language presents itself onto the surface of the image.
A file format, or encoding/decoding protocol, organises data according to a particular syntax, often to make the data that it took when the image was captured, smaller. These organisations are commonly referred to as compression algorithms (or language).
The choice of an image compression depends on its foreseen mode and place of usage; for instance, if the file is meant to be printed or redistributed digitally, another type of accuracy is necessary then when a software or hardware will render the image on screen.
In some cases, the image creator may choose not to use any compression at all, but instead to store the data as an unprocessed file. Images shot by professional photographers for instance, will be shot and stored in a RAW image file format. A RAW image file contains minimally processed data, which normally comes straight from the image sensor (for instance a CCD chip), in order to avoid any impurities (artifacts) that might be involved with image mediation, transcoding or compression.
︎Download the PDF
︎Polish translation by Bogumiła Piotrowska, Piotr Puldzian Płucienniczak, Aleksandra Pieńkosz
︎︎ flickr documentation
︎sonification workshop

A Vernacular of File Formats installed as part of the Stedelijk Museum Amsterdam Base show, Amsterdam, Netherlands, 2020.
The Vernacular of File Formats Archive (16GB of data) is part of the Base collection of Stedelijk Museum Amsterdam since 2016.
The Vernacular of File Formats Archive (16GB of data) is part of the Base collection of Stedelijk Museum Amsterdam since 2016.
 Pinakotheka Munich, Germany, 2023.
Pinakotheka Munich, Germany, 2023.  Order and Progress. Fabio Paris Gallery. Brescia, Italy. 2010.
Order and Progress. Fabio Paris Gallery. Brescia, Italy. 2010. Vernacular of File Formats ft. Kim Asendorfs Extrafile. Expositie for Re:Visie NFF augustus t/m 30 september 2011.
Vernacular of File Formats ft. Kim Asendorfs Extrafile. Expositie for Re:Visie NFF augustus t/m 30 september 2011.The Archive of the Vernacular of File Formats
In the winter of 2016, an 18.9 GB digital archive of A Vernacular of File Formats (edition of 3 plus 1 artist’s proof)—containing the original PDFs, a catalogue of databent images, video works, and related documentation—was jointly acquired by MOTI and the Stedelijk Museum Amsterdam.
To introduce the collection to the Stedelijk’s audience, I was commissioned to produce the video essay Where Should the Archive Begin and End?, which was published in Stedelijk Studies.
From the Introduction to the Vernacular:
When noise becomes filter art [ or when cool becomes hot ], (2010 / edited 2017)
Glitches are hot. It is clear from what we see on MTV, Flickr, in the club or in the bookstore: while the Glitch: Designing Imperfection (Moradi, 2009) coffee table book introduced a glitch design aesthetic to the world of latte drinking designers, Kanye West used a glitch aesthetic to illustrate his broken love life.
But while glitch design fulfills an average, imperfect stereotype, a filter or commodity that echoes a medium is the message-standard, naturally, the “No Content - Just Imperfection” slogan of hot glitch design is still complimented by cool glitches.
In "The Laws of Cool", Alan Liu asks himself: What is "Cool"? He describes that cool is the ellipsis of knowing what is cool, and withholding that idea. However, as Liu writes, those who insist on asking, are definitely uncool. In an effort to answer the question that cannot be answered, and come full circle on the ellipsis, I will try to give my take on what cool glitch can be. To me, cool glitch is represented by the glitches that do not (only) focus on a static end product, but (also) on a process, a personal exploration or a narrative element (that often reflects critically on a medium).
This is why cool is in a constant state of flux; it exists as an assemblage that consists of on the one hand the construction, operation and content of the apparatus (the medium) and on the other hand the work, the writer/artist, and the interpretation by the reader and/or user (the meaning). In the end, there is not one definition of cool glitch art, but many, which depend on the perspective chosen.
To make what was once cool now hot, or visa versa, and to take Designing Imperfection one step further, I hereby offer you A Vernacular of File Formats. In this PDF I describe the ways to exploit and deconstruct the organizations of file formats into new, brutalist designs.
…I am waiting for the first “Glitchs not dead“ peace of clothing in H&M. And because "fans are as bad as the ignorant", for the sake of being bad and ignorant, I will wear it!

 Catalogue descriptions by Domenico Quaranta for Order and Progress (solo show in Brescia at Gallery Fabio Paris in 2010).
Catalogue descriptions by Domenico Quaranta for Order and Progress (solo show in Brescia at Gallery Fabio Paris in 2010).








Vernacular of File Formats (2009-2010). Photoshop RAW, JPEG, JPEG 2000, PNG, BMP, Photoshop, TIFF, GIF, Targa.
Digital Prints on Dibond (matte finish).
Digital Prints on Dibond (matte finish).
Dear MR. Compression (2010)
Corrupt tango
There is not sufficient data.
Please enter data
Your file has invalid markers.
Enter new markers
Your dimensions do not correspond.
Change dimensions
ERROR
Goto data therapy and repair your registry
Your keyframes are missing
Your codecs are not supported
Please respect the software
Now it is too little too late [system shut down]
Dear mr compression
I write a 1000 poems to you
Is this what they call progress?
Warmly yours,
the noxious angel of history
Corrupt tango
There is not sufficient data.
Please enter data
Your file has invalid markers.
Enter new markers
Your dimensions do not correspond.
Change dimensions
ERROR
Goto data therapy and repair your registry
Your keyframes are missing
Your codecs are not supported
Please respect the software
Now it is too little too late [system shut down]
Dear mr compression
I write a 1000 poems to you
Is this what they call progress?
Warmly yours,
the noxious angel of history
Why make (another) ‘glitch’ software
Realize that the gospel of Glitch Art also tells about new standards implemented by corruption. Not all Glitch Art is progressive or something new. The popularization and cultivation of the avant-garde of mishaps has become predestined and unavoidable. Be aware of easily reproducible glitch effects, automated by softwares and plug-ins. What is now a glitch will become a fashion.**
What I find today in the Glitch Art Flickr pool, are images opposing my original definitions of glitch - a short-lived fault in a system, inducing affect such as surprise or shock - and glitch art - work that makes us critically and radically challenge normative knowledge, values, habits and expectations. Instead, glitch art has become more and more like a style, or even a genre.
While glitch art as a style recalls Homi Bhabhas': "almost the same, but not quite" or “mimicry of digital slippage”, the ‘real’ glitch in glitch art has slowly diminished into a virtual signifier. The by popular culture commodified side of glitch has become a primal part of a new ‘glitch-economy’, which has left me to be believe I should pay more attention to this 'other side of the coin'.
This is why I decided to teach about the materiality of file formats; their different languages, slang or dialects, and how these specific qualities, rules and rhetorics can be exploited as a generative matter to create new images (a practice closely related to databending). I named the workshop "A Vernacular of File Formats" and showed different compression based artworks, while supplying the students with methods and tools to create their own format based research, and possibly art and design.
One of the troubles I ran into during the workshop was that the tools I had were not ideal for such a workshop; with every other file format we set out to manipulate we had to switch softwares, which between the different OSs' on the students computers became a real *pain*.
When I spoke to Johan Larsby (the creator of Swutits) about the lack of software, he proposed a collaboration - which is how the Monglot project started.
︎ Monglot only worked on MacOS 10.5 and 10.6. In 2016 KernelEquinox opensourced a program inspired by Monglot for Windows -> ︎
︎ More about monglot and its strange interface here
︎ Download Monglot, code, Monglot master
︎ Monglot only worked on MacOS 10.5 and 10.6. In 2016 KernelEquinox opensourced a program inspired by Monglot for Windows -> ︎
︎ More about monglot and its strange interface here
︎ Download Monglot, code, Monglot master
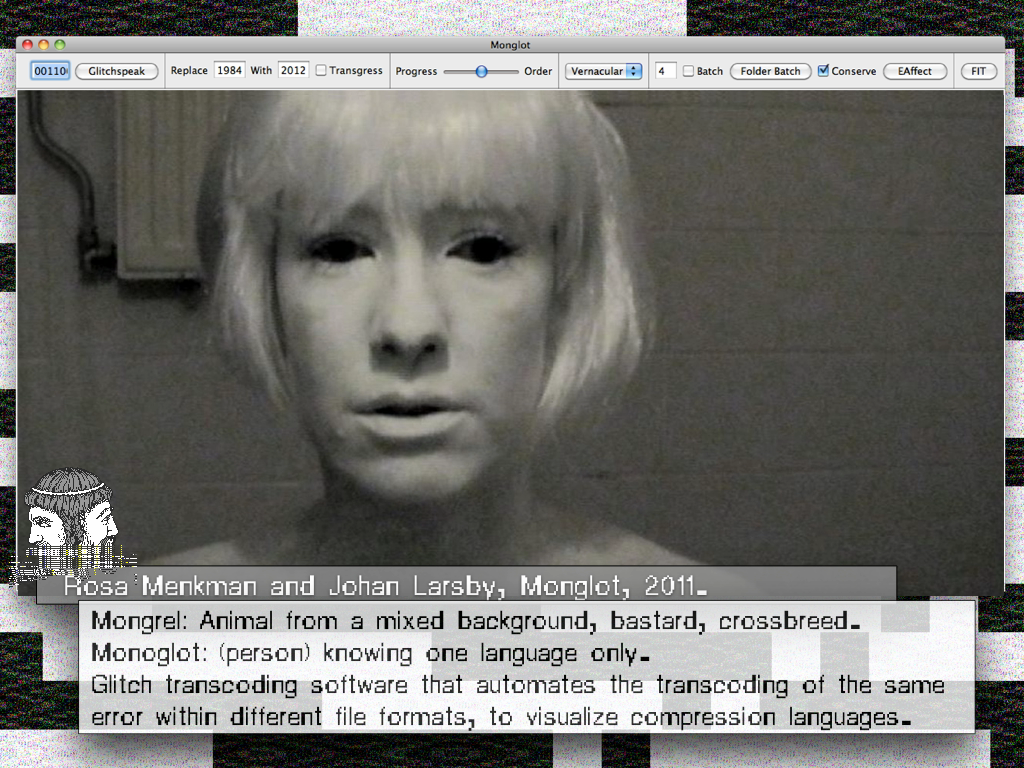
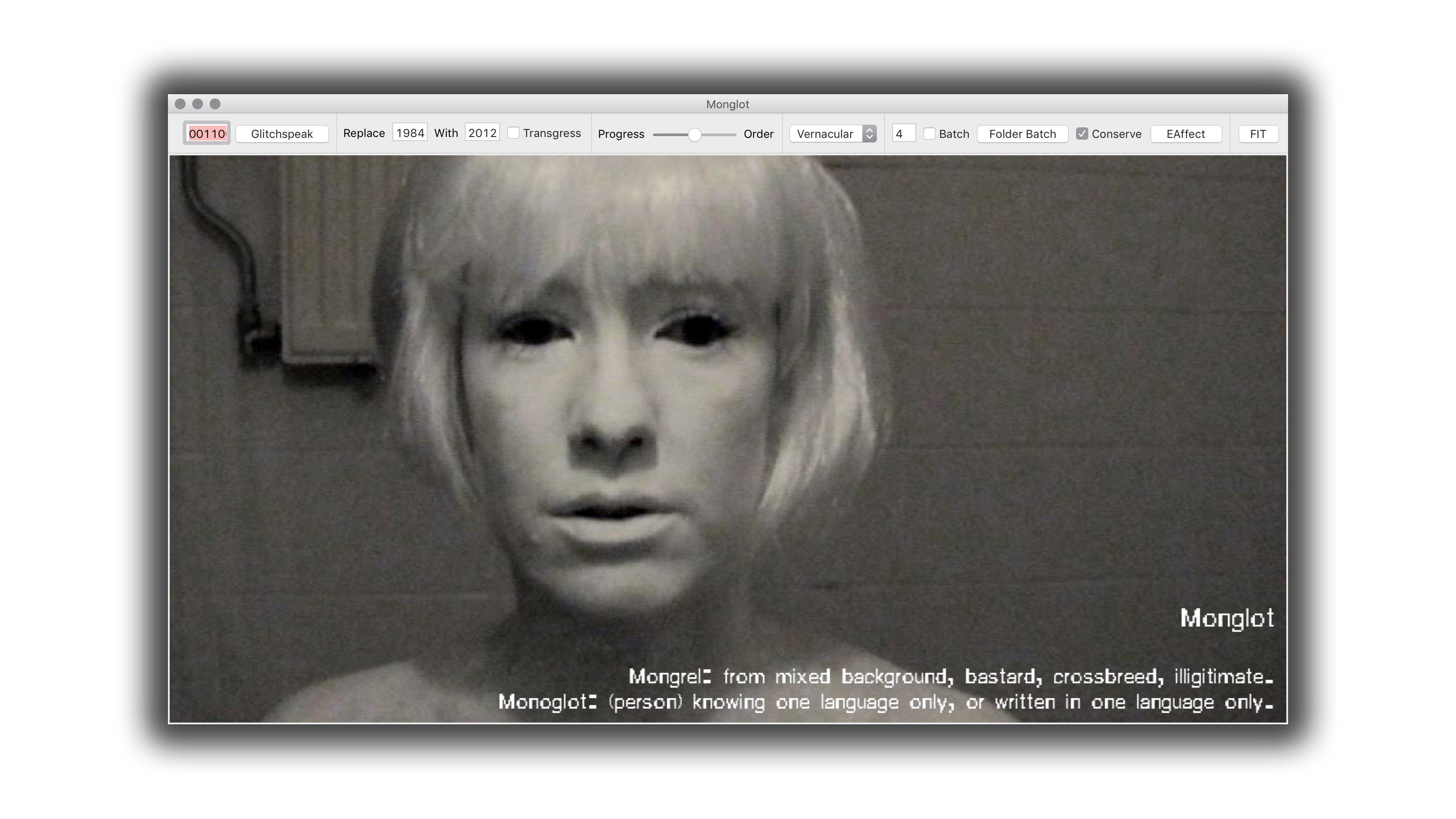
Monglot (2011)
A Glitch Software collaboration with Johan Larsby (SE) 2011.
Of Mimicry and Glitch Art: The Ambivalence of a 'Colonial' Glitch Art discourse
(order and progress || chaos and destruction)
The name Monglot is a degeneration of the terms Mongrel and Monoglot (the term also references Homi Bhabha's "forked tongue" of colonialism and something I would like to refer to as Glitch Speak).
*/
Mongrel: the offspring of a variety of species, of mixed background, bastard, or imperfect crossbreed
Mongrel: the offspring of a variety of species, of mixed background, bastard, or imperfect crossbreed
Monoglot: knowing only one language; monolingual.
*/
*/
Generally, glitch aesthetics or compression artifacts such as fragmentation, grain, ghosting, heterodynes, interlacing, jitter, jaggies, (…) posterization, pixelating, quantization error, ringing, staircase noise, scan lines (…) come to the surface because of an accidental flaw in the image data, which shows on the surface of the image itself.
The Monglot software generates glitches. It does this by adding a random or chosen error to the image-data, which is encoded via a compression language of choice. This error than sits on the surface of the image. In doing so Monglot mashes two languages together: the language of the compression and the visual image itself.
While for most glitch softwares the final product is the focus, Monglot focusses on the /experimental/, generative part of glitching.
By comparing different file formats and their behaviors, Monglot can be used to learn and research about file formats.
Monglot aims to show the ambivalence (cool vs. hot) and the double articulation (encoding vs. image data) of (file format-based) Glitch Art.
The user of Monglot is able to repeat an error by clicking ‘Glitchspeak’ or chose a particular error on the ‘Replace’ function of the software. This is how Monglot exists as a compromise in-between cool and hot.
The user of Monglot is able to repeat an error by clicking ‘Glitchspeak’ or chose a particular error on the ‘Replace’ function of the software. This is how Monglot exists as a compromise in-between cool and hot.
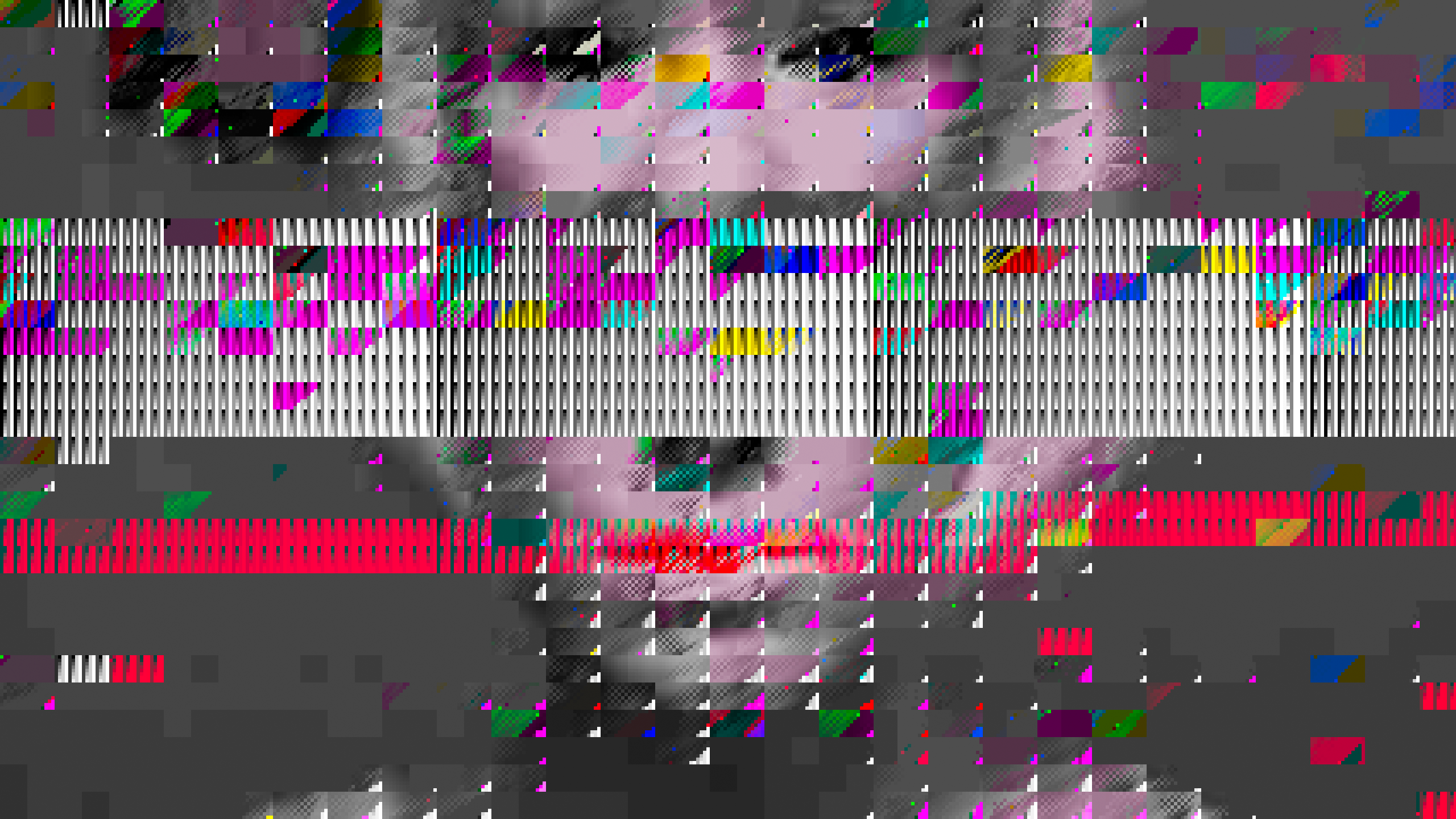

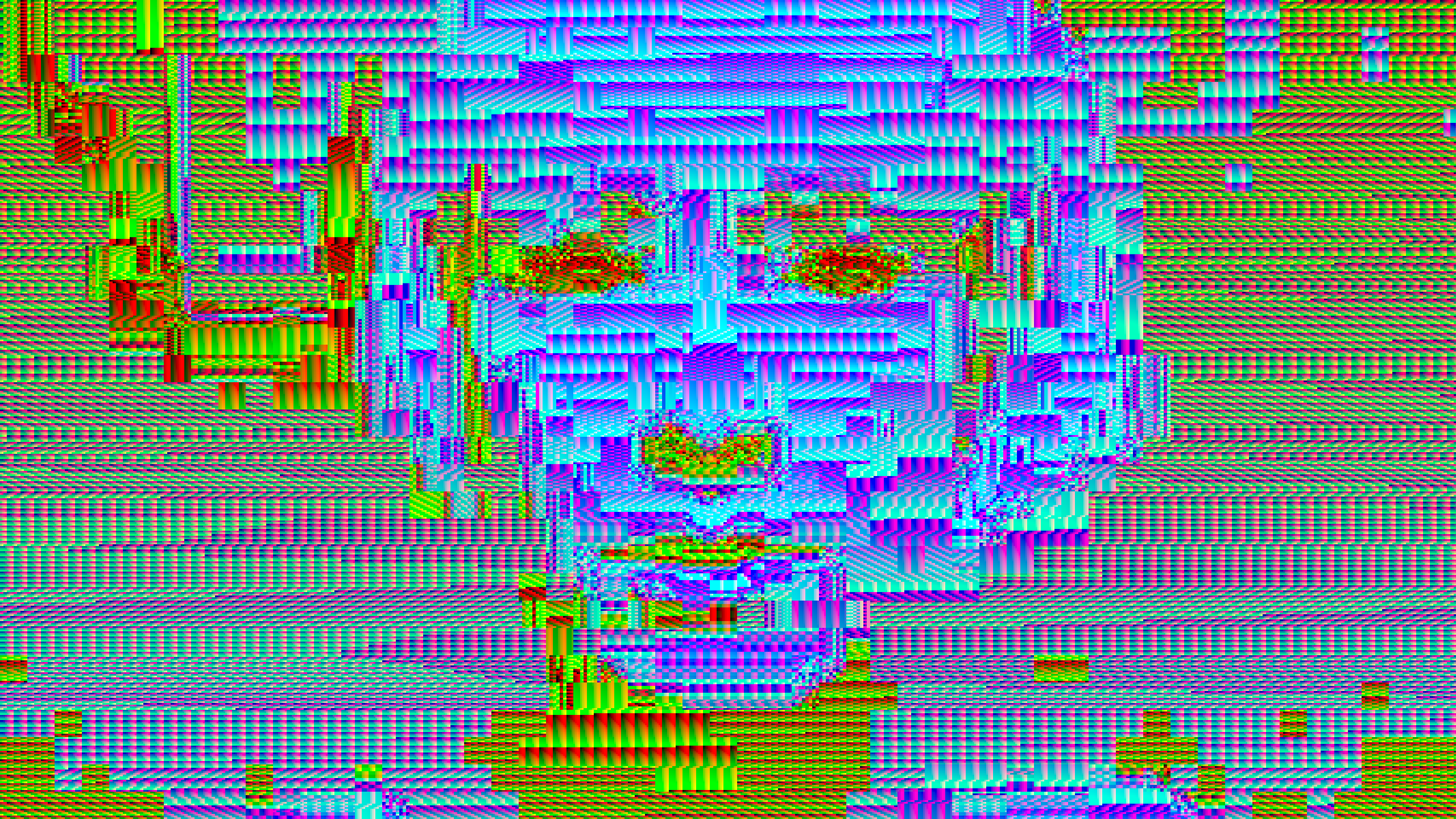



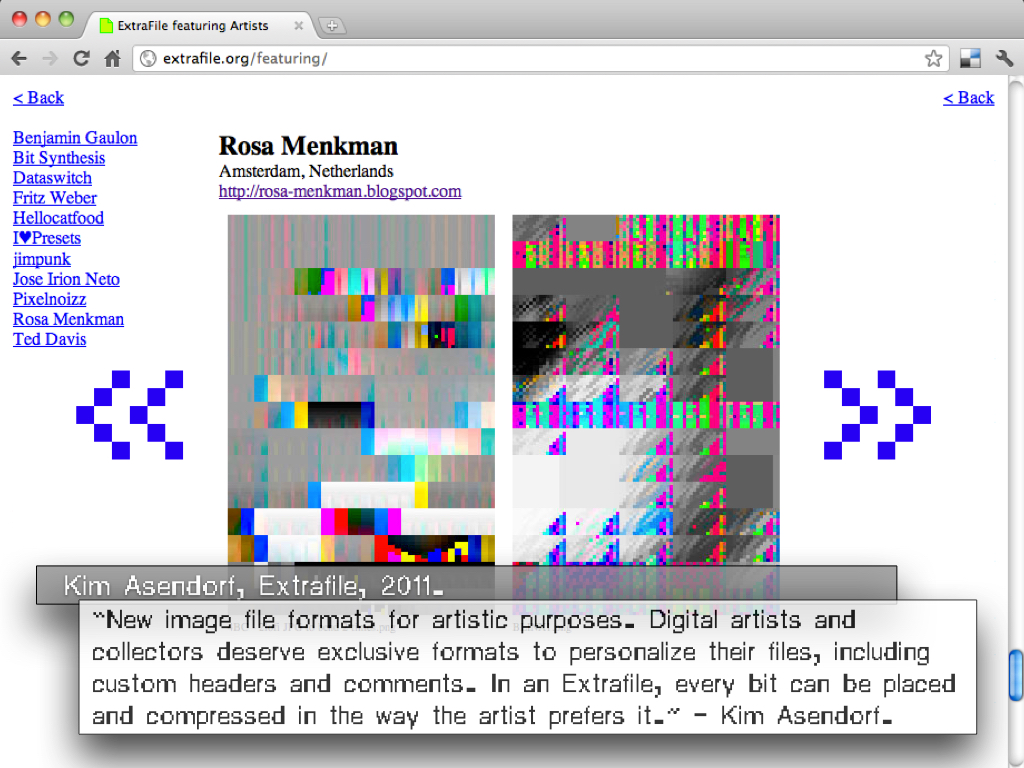
Extrafile (2011)
Extrafile vs. Monglot: a commission for Kim Asendorf, 2011. ︎
From the Extrafile project wesbite:
ExtraFile is conceptual software art with a practical usage, developed in 2011 by Kim Asendorf.
Its main intention is to wiggle the static system of image file formats.
Extrafile started with the idea of inventing a new image file format, a format as a piece of art, far away from the mainstream and commercial standards. A format that would exist just to express the feeling of using and saving data in a new, fictitious or artificial way and bringing the filename extension into the scope of the artwork itself. In simple terms: Creating an exclusivity.
The freedom not to have to pay attention to the file size or the loading and saving times provides the option to implement artistically byte orders, odd quality behaviors and visual designed formats.
ExtraFile is breaking the rules of commercial formats like JPG, PNG or TIFF. It is a pioneer art project in storing image data. The process and the resulting bytes, regardless of content, become the artwork itself.
You want painters to build their own canvas?
Digital artists and collectors deserve exclusive formats. Personalized files, including costume headers or comments. Every bit could be placed like the artist wants it.
ExtraFile is a native Mac OS X image converter application with the ability to open, preview and save the most common image file formats. It offers the possibility to use the seven build-in formats, 4Bit Components, Block Ascii, Block Indexed, Channel Compressed Image, Monochrome Collector File, Uniform Spectrum and the ExtraFile Format, to store image data.
ExtraFile is an open source project,
the source code is available on GitHub under the Artistic License 2.0.
Notes, comments and related projects:
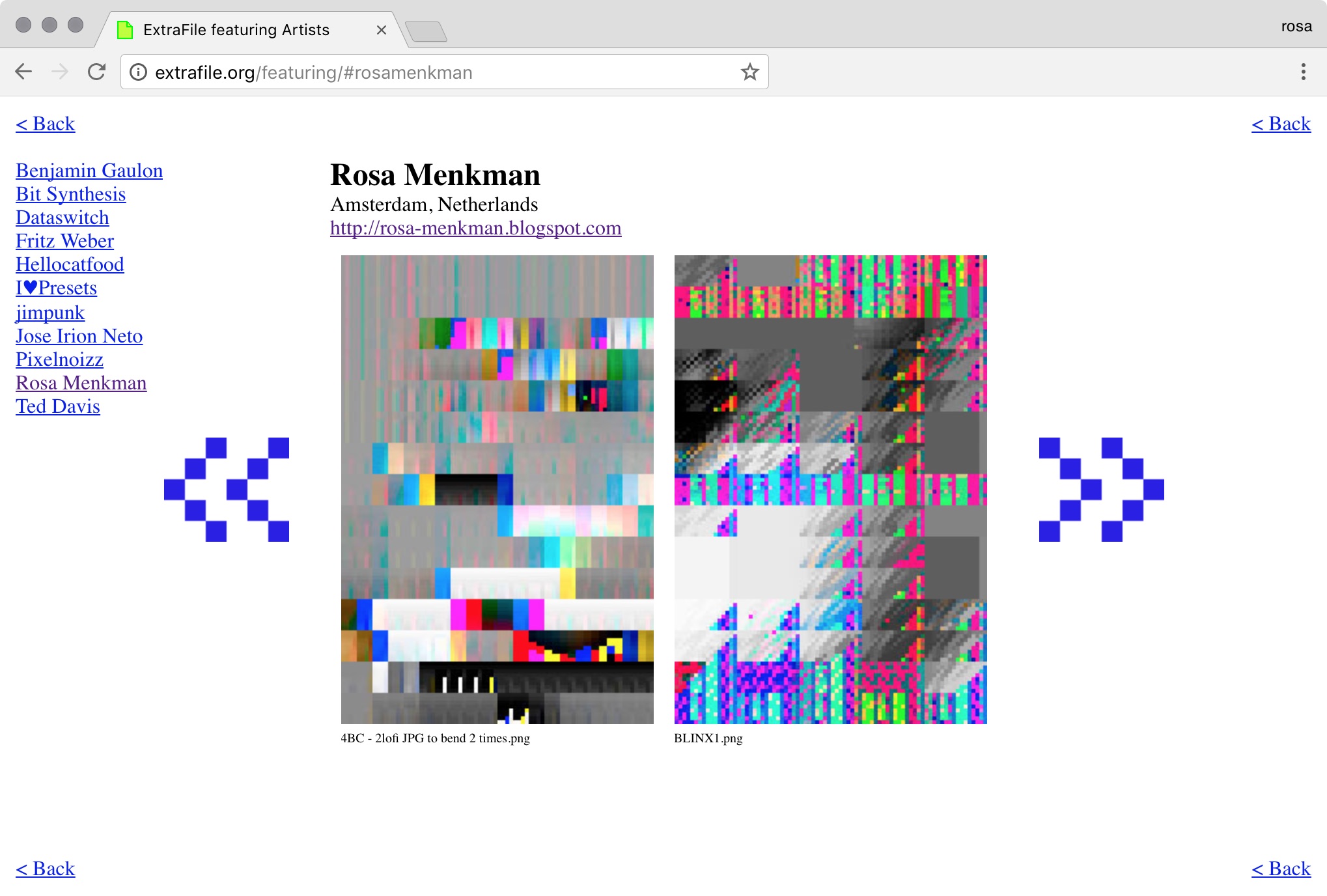
Extrafile vs GLI.TC/H Extrafile vs. A Vernacular of File Formats by Rosa Menkman
Extrafile - tiff > cci / bmp > cci by Jose Irion Neto
when we ran out of formats, there was ExtraFile by Bit Synthesis
EXTRAFILE by Hellocatfood
extrafile by Pixelnoizz
.

WRITTEN (THEORY)
>>> APPROP/R/PIRATE
>>> BEHIND WHITE SHADOWS (OF IMAGE PROCESSING) (2017)
>>> ADDENDUM (2017)
>>> APPROP/R/PIRATE
>>> BEHIND WHITE SHADOWS (OF IMAGE PROCESSING) (2017)
>>> ADDENDUM (2017)
ARTWORKS (PRACTICE)
>>> Pique Nique pour les Inconnues (2017 - 2020)
>>> The i.R.D Perfect DE/CALIBRATION ARMY and 365PERFECT (2017 - ...)
>>> PATCH (for the i.R.D Perfect DE/CALIBRATION ARMY) (2017)
>>> Pique Nique pour les Inconnues (2017 - 2020)
>>> The i.R.D Perfect DE/CALIBRATION ARMY and 365PERFECT (2017 - ...)
>>> PATCH (for the i.R.D Perfect DE/CALIBRATION ARMY) (2017)

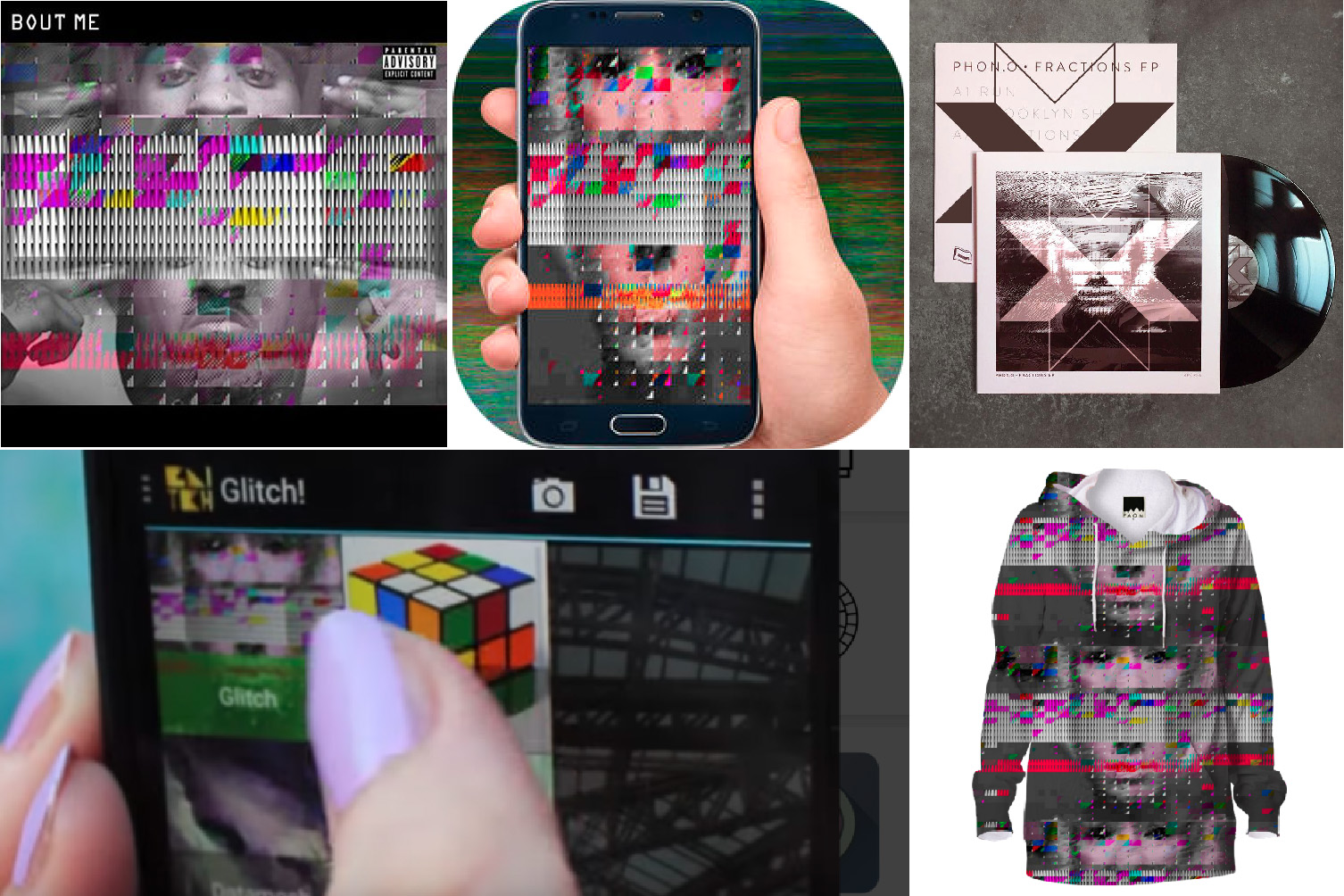
Over the years, I have found many different copies of the image of my face (hailing from the Vernacular of File Formats) used both with and without permission or accreditation.
>Here< you can find a small collection of examples
I believe and publish with a Copy <it> Right ethic:
To me, copying as a creative, exploratory, and educational act is free and encouraged, provided proper accreditation is given. However, when copying becomes commodification and profit is anticipated, explicit permission must be sought and compensation may be requested.
As I began finding my face on commercially available objects, commodified and uncredited, I wondered what it meant to lose authorship and ownership of my face, and whether historical precedents exist.
During my research I came across the stories of color test cards: photographs of Caucasian women used to calibrate analog and digital image-processing technologies. These women have been reused endlessly, yet very little—sometimes not even their names—is known about them.
>Here< you can find a small collection of examples
I believe and publish with a Copy <it> Right ethic:
First, it’s okay to copy! Believe in the process of copying as much as you can; with all your heart is a good place to start – get into it as straight and honestly as possible. Copying is as good (I think better from this vector-view) as any other way of getting ’there.’
NOTES ON THE AESTHETICS OF ‘copying-an-Image Processor’
– Phil Morton (1973).
To me, copying as a creative, exploratory, and educational act is free and encouraged, provided proper accreditation is given. However, when copying becomes commodification and profit is anticipated, explicit permission must be sought and compensation may be requested.
As I began finding my face on commercially available objects, commodified and uncredited, I wondered what it meant to lose authorship and ownership of my face, and whether historical precedents exist.
During my research I came across the stories of color test cards: photographs of Caucasian women used to calibrate analog and digital image-processing technologies. These women have been reused endlessly, yet very little—sometimes not even their names—is known about them.
This resulted in the research essay Behind White Shadows, which was published in:
Behind White Shadows essay for solo show (TRANSFER gallery, NY, 2017)
Faceless, De Gruyter, 2018 (ed: Bogomir Doringer)
Performing the System (ed: Nora Brünger, Luzi Gross, Torsten Scheid: 2019, Universitätsverlag Hildesheim)
Computer Grrls (ed. Inke Arns, HMKV, 2021)
Behind White Shadows was also featured in the Cyberfeminism Index (ed. Mindy Sue, 2023)
Behind White Shadows essay for solo show (TRANSFER gallery, NY, 2017)
Faceless, De Gruyter, 2018 (ed: Bogomir Doringer)
Performing the System (ed: Nora Brünger, Luzi Gross, Torsten Scheid: 2019, Universitätsverlag Hildesheim)
Computer Grrls (ed. Inke Arns, HMKV, 2021)
Behind White Shadows was also featured in the Cyberfeminism Index (ed. Mindy Sue, 2023)
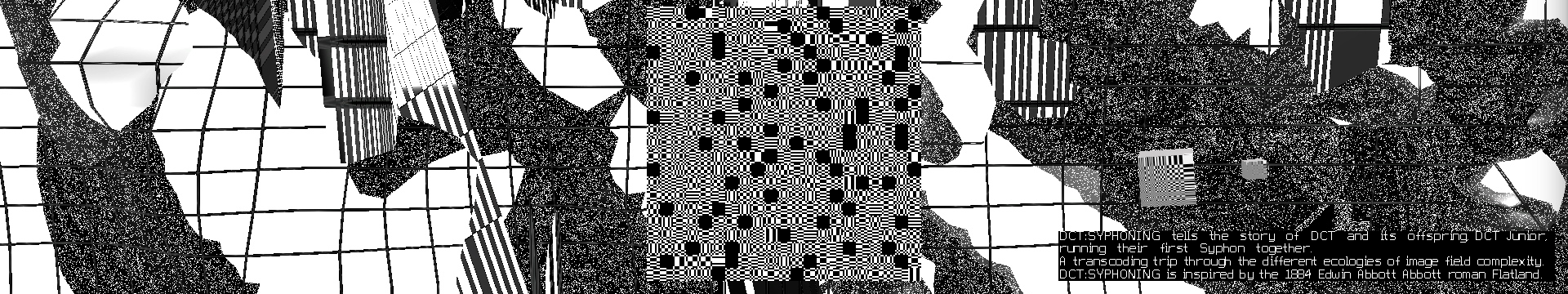
DCT:SYPHONING (2015-2017)
DCT is the key algorithm in JPEG compression, that converts 8x8 blocks of pixel intensities into 64 frequency components.
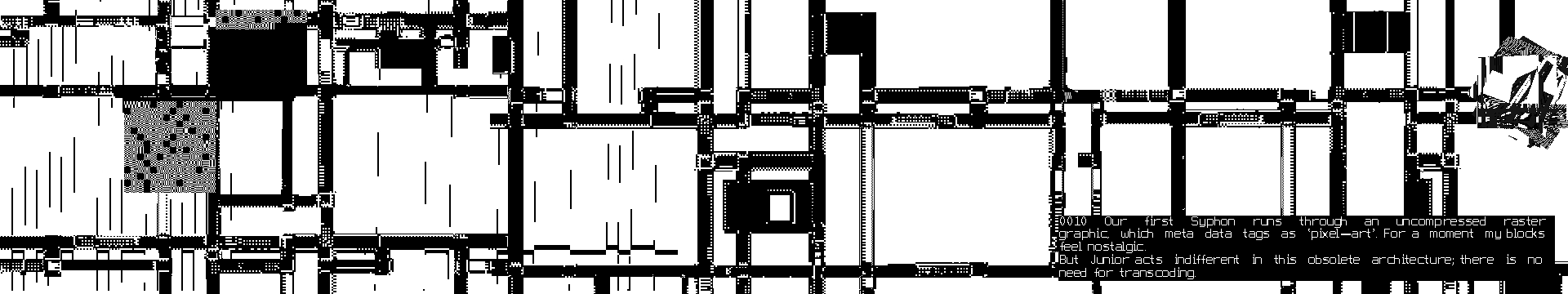
In DCT:SYPHONING, an anthropomorphised DCT (Senior) narrates its first SYPHON (data transfer) together with DCT Junior, and their interactions as they translate data from one image compression to a next (aka the “realms of complexity”).
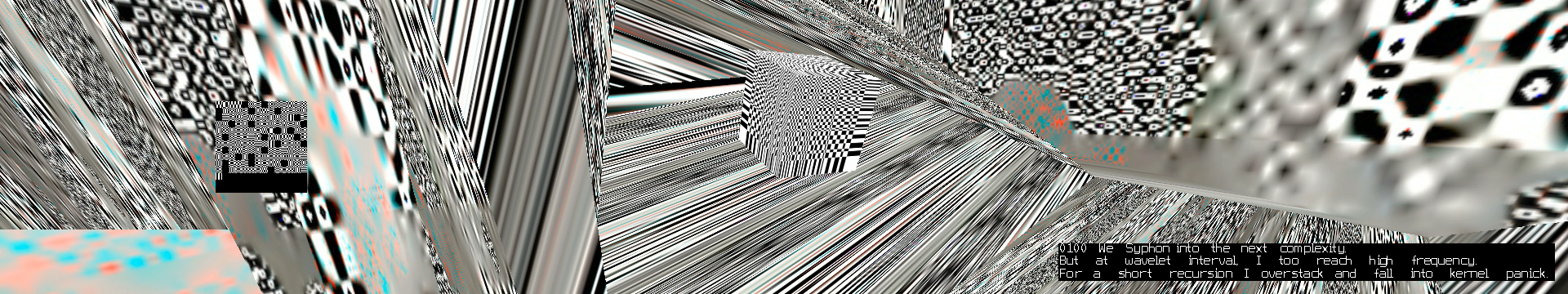
As Senior introduces Junior to the different levels of image complexity, they move from blocks (the realm in which they normally resonate), to dither, lines and the more complex realms of wavelets and vectors. Junior does not only react to old compressions technologies, but also the newer, more complex ones which ‘scare' Junior, because of their 'illegibility'.
WRITTEN (THEORY)
>>> DCT: THE GUY BEHIND THE GUY BEHIND THE GUY (2015)
or: How Not to be Read (a recipe using Discrete Cosine Transform) [ pdf ]
SEMINAR SLIDES
>> ALT.HISTORY (A Genealogy of Macroblocks)
ARTWORKS (PRACTICE)
>>> An Ecology of Compression Complexities (2017)
>>> DCT:SYPHONING. The 1000000th (64th) interval (2015 - 2017)
>>> DCT (CRYPTOGRAPHY) (2015)
>>> i.R.D. PATCH (with DCT key) (2015)
from one plane of complexity (2017)
A map of the different complexities of compression artifacts drawn by the Angel of History.
The map features the realms of:
⦁ Dots
(pixels, dither, coordinates)
━ Lines
(interlacing, interleaving, scan line, border, beam)
▩ Blocks
(macroblocks, cluster)
⌇ Wavelets
(JPEG2000)
⟗ Vectors
(3D obj, time encoding in MPEG4)
BLOBS
The map features the realms of:
⦁ Dots
(pixels, dither, coordinates)
━ Lines
(interlacing, interleaving, scan line, border, beam)
▩ Blocks
(macroblocks, cluster)
⌇ Wavelets
(JPEG2000)
⟗ Vectors
(3D obj, time encoding in MPEG4)
BLOBS

DCT:SYPHONING: The 1000000th (64th) interval. (2015-2017)
VR WALKTHROUGH SCREENCAPTURE, rendered in 2017.
DCT:SYPHONING came about during my research into the ecology of compression complexities.

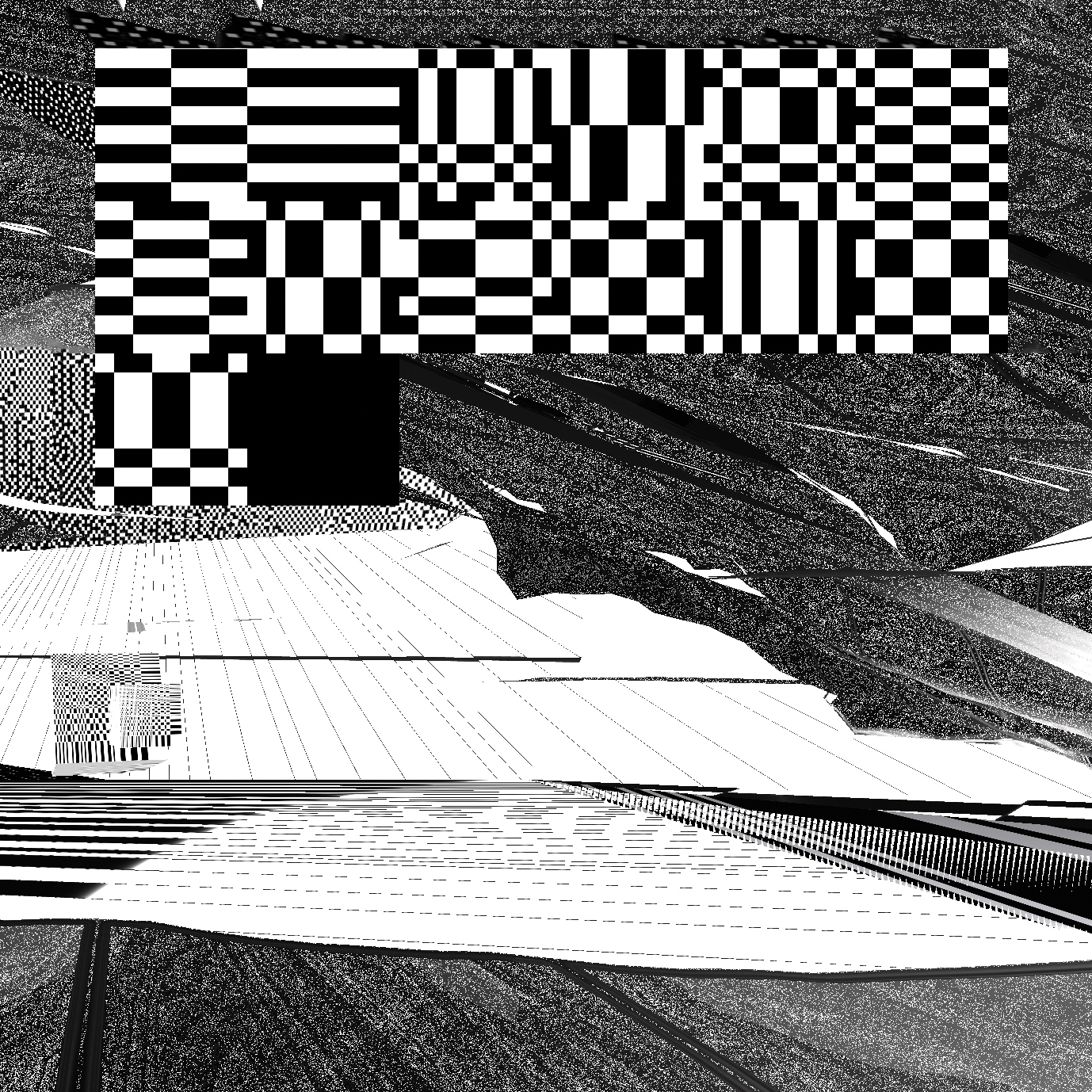

In DCT:SYPHONING, an anthropomorphised DCT (Senior) narrates its first SYPHON (data transfer) together with DCT Junior, and their interactions as they translate data from one image compression to a next (aka the “realms of complexity”).
As Senior introduces Junior to the different levels of image complexity, they move from blocks (the realm in which they normally resonate), to dither, lines and the more complex realms of wavelets and vectors. Junior does not only react to old compressions technologies, but also the newer, more complex ones which ‘scare' Junior, because of their 'illegibility'.
☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰
DCT:SYPHONING is a contemporary translation of the 1884 Edwin Abbott Abbott roman “Flatland”. The work describes some of the algorithms at work in digital image compression.
Inspired by SYPHON, an open source software by Tom Butterworth and Anton Marini.
![]()
DCT:SYPHONING 3 SCREENS AT NXT, AMSTERDAM, 2025.
![]()
DCT:SYPHONING at JMAF, Tokyo, Japan, 2017
PDF Version full edition of Lune Magazine 3 can be downloaded here:
https://lunejournal.org/03-display/
guest edited by Nathan Jones
https://alittlenathan.co.uk/
Spanish Translation
>>
As Senior introduces Junior to the different levels of image complexity, they move from blocks (the realm in which they normally resonate), to dither, lines and the more complex realms of wavelets and vectors. Junior does not only react to old compressions technologies, but also the newer, more complex ones which ‘scare' Junior, because of their 'illegibility'.
☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰
DCT:SYPHONING is a contemporary translation of the 1884 Edwin Abbott Abbott roman “Flatland”. The work describes some of the algorithms at work in digital image compression.
Inspired by SYPHON, an open source software by Tom Butterworth and Anton Marini.
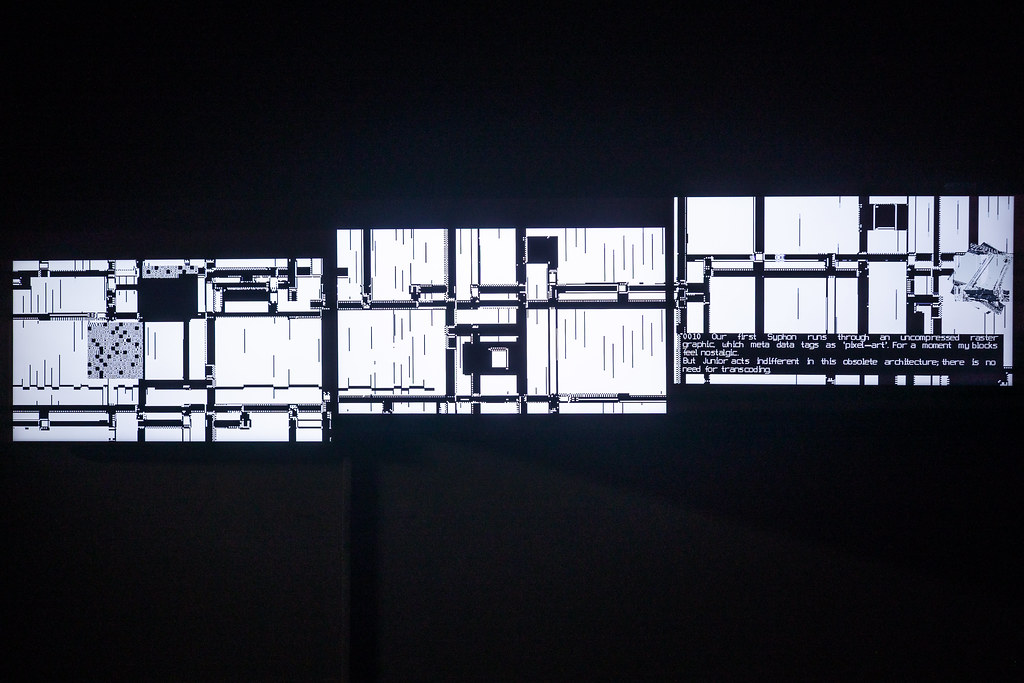
DCT:SYPHONING 3 SCREENS AT NXT, AMSTERDAM, 2025.

DCT:SYPHONING at JMAF, Tokyo, Japan, 2017
PDF Version full edition of Lune Magazine 3 can be downloaded here:
https://lunejournal.org/03-display/
guest edited by Nathan Jones
https://alittlenathan.co.uk/
Spanish Translation
>>
Production of DCT:SYPHONING
DCT:SYPHONING was first commissioned by the Photographers Gallery in London, for the show Power Point Polemics. This version was on display as a Powerpoint Presentation; a .ppt (Jan - Apr 2016).
A 3 channel video installation was conceived for the 2016 Transfer Gallery's show "Transfer Download", first installed at Minnesota Street Project in San Francisco (July - September, 2016)
DCT:SYPHONING released as VR, commissioned as part of DiMoDA’s Morphé Presence and later as stand alone (2017).
>>
![]()
DCT:SYPHONING @the Current museum for contemporary art, NY, USA
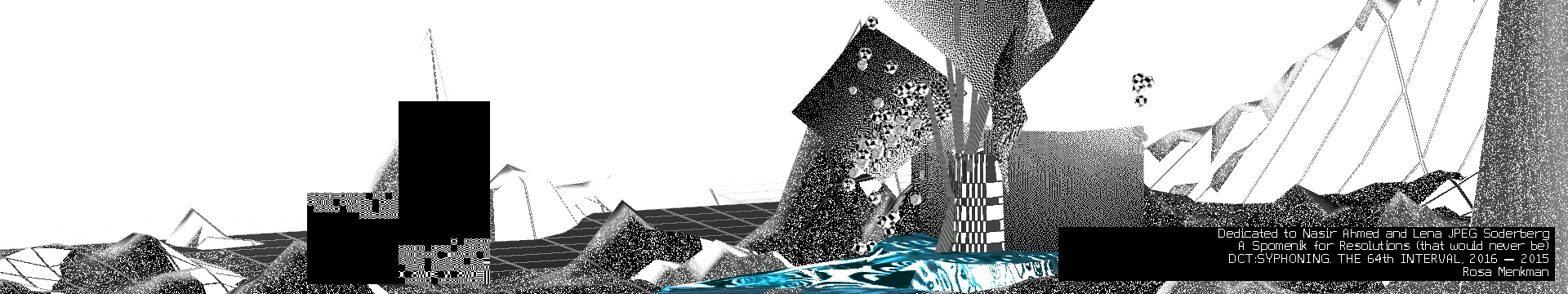
In my solo show Behind White Shadows, DCT:SYPHONING was projected on a 4 meter high custom build spomenik (memorial)
DCT:SYPHONING was first commissioned by the Photographers Gallery in London, for the show Power Point Polemics. This version was on display as a Powerpoint Presentation; a .ppt (Jan - Apr 2016).
A 3 channel video installation was conceived for the 2016 Transfer Gallery's show "Transfer Download", first installed at Minnesota Street Project in San Francisco (July - September, 2016)
DCT:SYPHONING released as VR, commissioned as part of DiMoDA’s Morphé Presence and later as stand alone (2017).
>>

DCT:SYPHONING @the Current museum for contemporary art, NY, USA
In my solo show Behind White Shadows, DCT:SYPHONING was projected on a 4 meter high custom build spomenik (memorial)






<*href: Cory Arcangel: on Compression, 2007>
A Discrete Cosine Transform or 64 basis functions of the JPEG compression (Joint Photographic Experts Group) 8 x 8 pixel macroblocks.
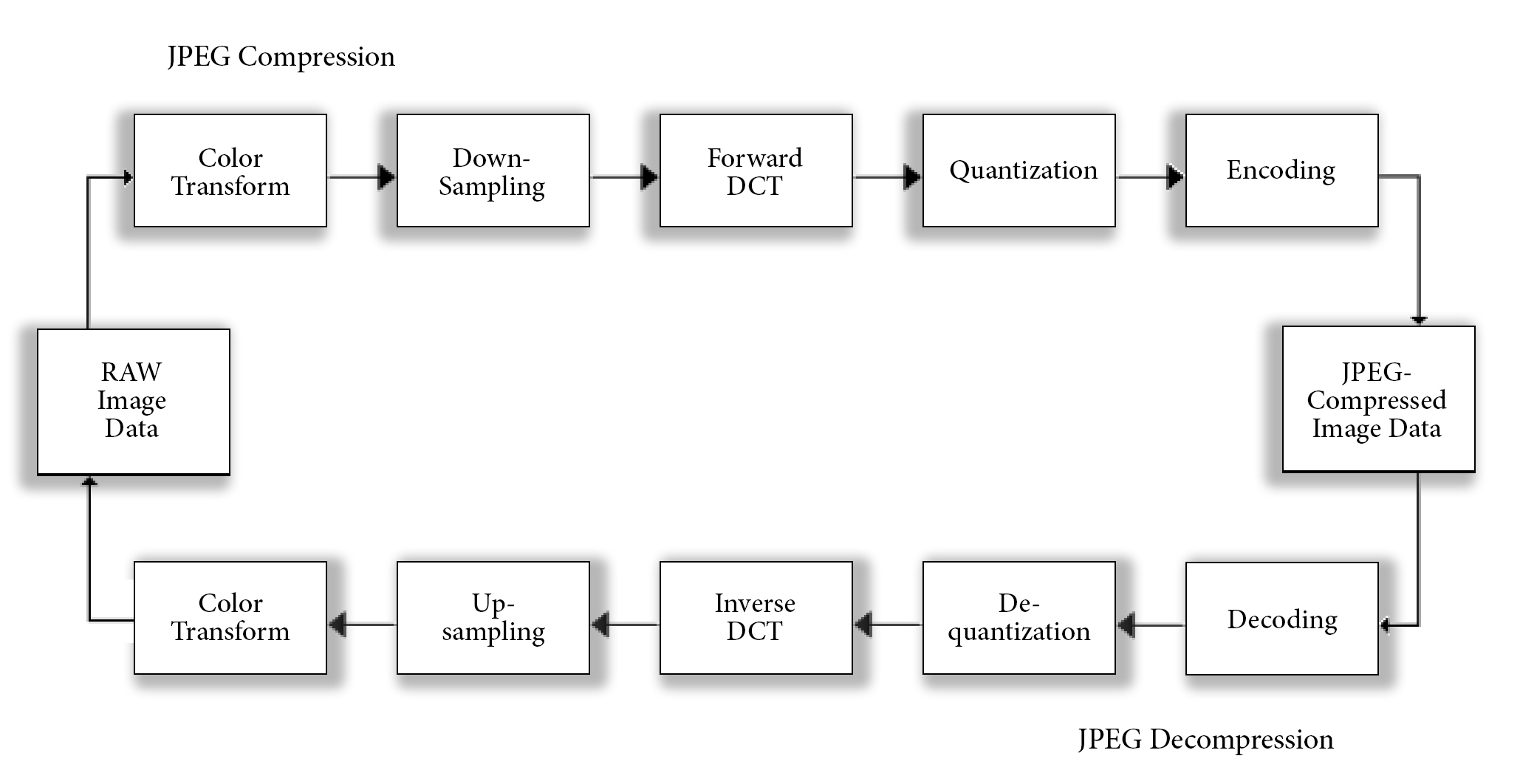 The .JPEG compression consists of these six subsequent steps
The .JPEG compression consists of these six subsequent steps
1. Color space transformation. Initially, the image has to be transformed from the RGB colorspace to
Y′CbCr. This colorspace consists of three components that are handled separately; the Y’ (luma or brightness) and the Cb and Cr values; the blue-difference and red-difference Chroma components.
2. Downsampling. Because the human eye doesn’t perceive small differences within the Cb and Cr space very well, these elements are downsampled, a process that reduces its data dramatically.
3. Block splitting. After the colorspace transformation and downsampling steps, the image is split into 8 x 8 pixel tiles or macroblocks, which are transformed and encoded separately.
4. Discrete Cosine Transform. Every Y’CbCr macroblock is compared to all 64 basis functions (base cosines) of a Discreet Cosine Transform. A value of resemblance per macroblock per base function is saved in a matrix, which goes through a process of reordering.
5. Quantization. The JPEG compression employs quantization, a process that discards coefficients with values that are deemed irrelevant (or too detailed) visual information. The process of quantization is optimized for the human eye, tried and tested on the Caucasian Lena color test card.
Effectively, during the quantization step, the JPEG compression discards most of all information within areas of high frequency changes in color (chrominance) and light (luminance), also known as high contrast areas, while it flattens areas with low frequency (low contrasts) to average values, by re-encoding and deleting these parts of the image data. This is how the rendered image stays visually similar to the original – least to human perception. But while the resulting image may look similar to the original, the JPEG image compression is Lossy, which means that the original image can never be reconstructed.
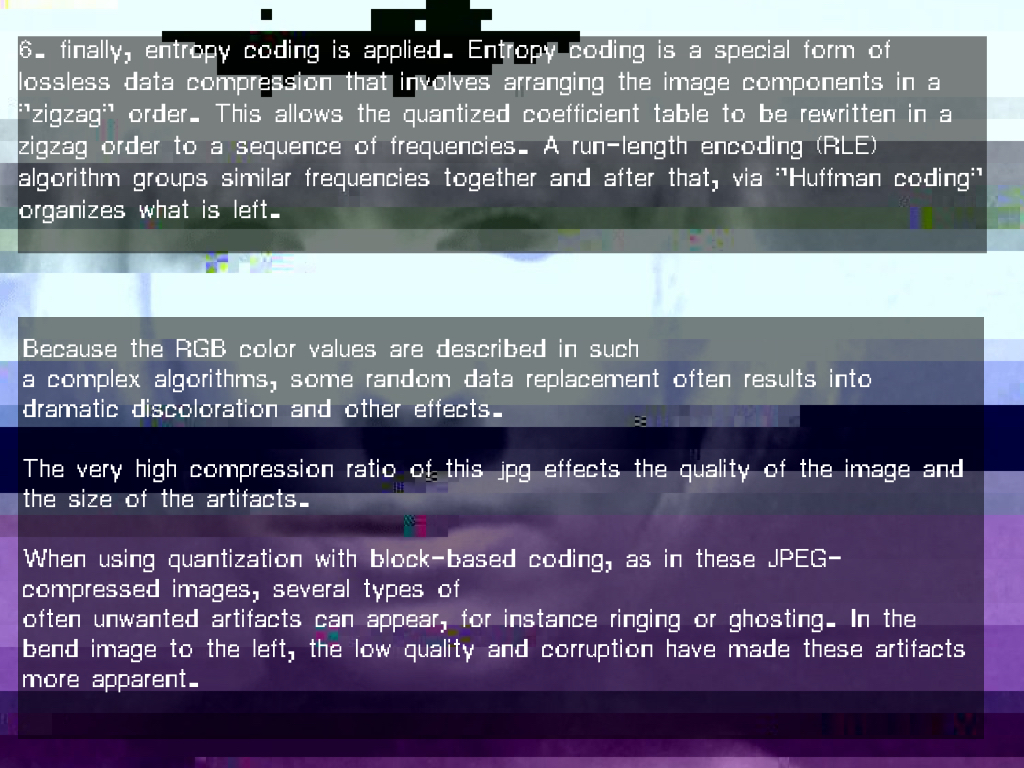
6. Entropy coding. Finally, a special form of lossless compression arranges the macroblocks in a zigzag order. A Run-Length Encoding (RLE) algorithm groups similar frequencies together while Huffman coding organizes what is left.
 Revealing the surface and structure of the image *
Revealing the surface and structure of the image *<href: Ted Davis: ffd8, 2012>
A side effect of the JPEG compression is that the limits of the images’ resolution – which involve not just the images’ number of pixels in length and width, but also the luma and chroma values, stored in the form of 8 x 8 pixel macroblocks – are visible as artifacts when zooming in beyond the resolution of the JPEG.
Because the RGB color values of JPEG images are transcoded into Y’CbCr macroblocks, accidental or random data replacements can result into dramatic discoloration or image displacement. Several types of artifacts can appear; for instance ringing, ghosting, blocking, and staircase artifacts. The relative size of these artifacts demonstrates the limitations of the JPEGs informed data: a highly compressed JPEG will show relatively larger, block-sized artifacts.

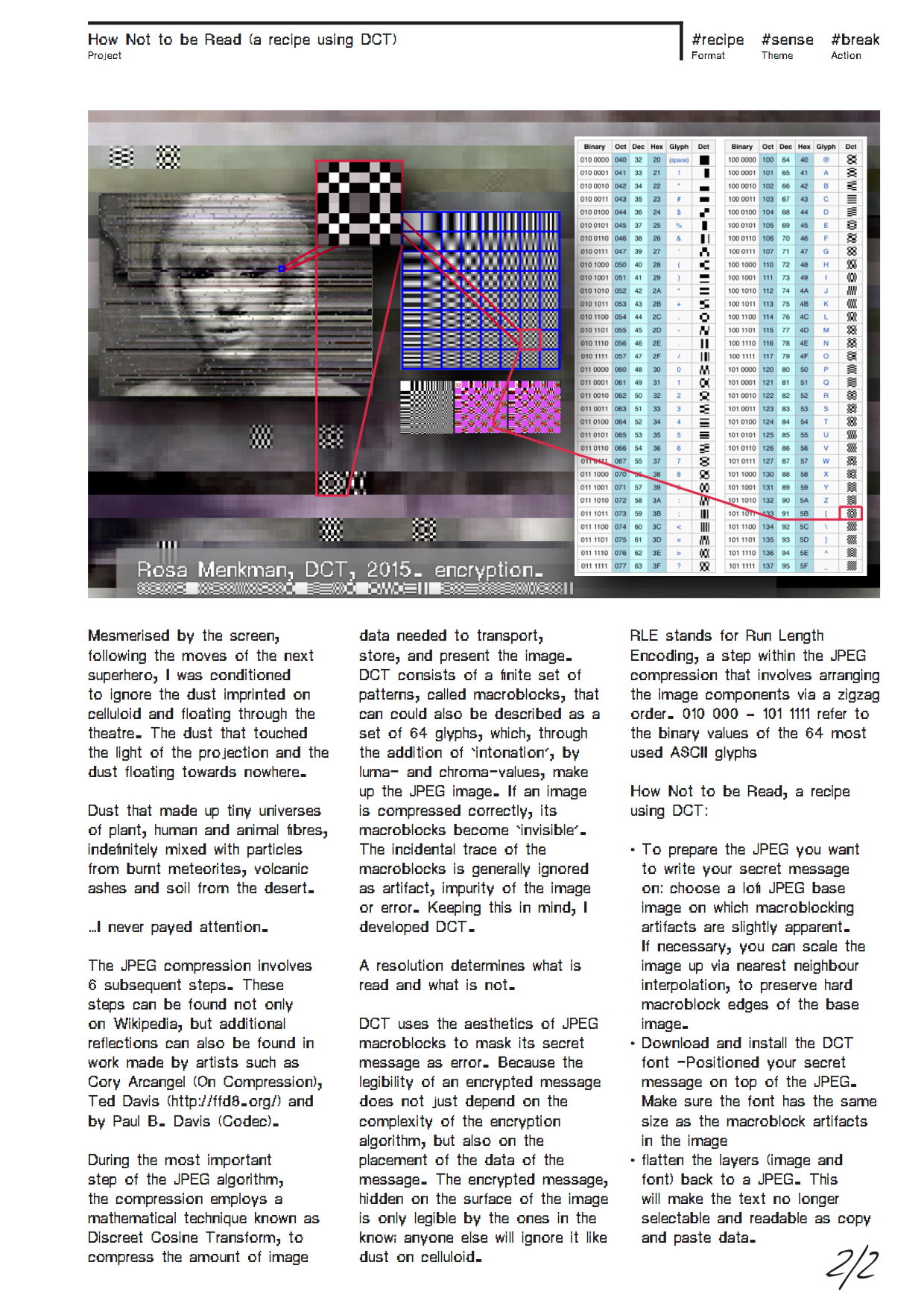
HOW NOT TO BE READ* [ a recipe using DCT ENCRYPTION ]
<href: Hito Steyerl: How Not to Be Seen, 2013>
The legibility of an encrypted message does not just depend on the complexity of the encryption algorithm, but also on the placement of the data of the message. Here they are closely connected to resolutions: resolutions determine what is read and what is unseen or illegible.
DCT ENCRYPTION (2015) uses the aesthetics of JPEG macroblocks to mask its secret messages on the surface of the image, mimicking error. The encrypted message, hidden on the surface is only legible by the ones in the know; anyone else will ignore it like dust on celluloid.
While the JPEG compession consists of 6 steps, the basis of the compression is DCT, or Discrete Cosine Transform. During the final, 6th step of the JPEG compression, entropy coding, a special form of lossless data compression, takes place. Entropy coding involves the arranging the image components in a "zigzag" order, using run-length encoding (RLE) to group similar frequencies together.
How Not to be Read, a recipe using DCT:
︎ for the #3D Additivist Cookbook.
︎ DCT won the Crypto Desgin Challenge Award in 2015.
<href: Hito Steyerl: How Not to Be Seen, 2013>
A PDF with this work is downloadable here
The legibility of an encrypted message does not just depend on the complexity of the encryption algorithm, but also on the placement of the data of the message. Here they are closely connected to resolutions: resolutions determine what is read and what is unseen or illegible.
DCT ENCRYPTION (2015) uses the aesthetics of JPEG macroblocks to mask its secret messages on the surface of the image, mimicking error. The encrypted message, hidden on the surface is only legible by the ones in the know; anyone else will ignore it like dust on celluloid.
While the JPEG compession consists of 6 steps, the basis of the compression is DCT, or Discrete Cosine Transform. During the final, 6th step of the JPEG compression, entropy coding, a special form of lossless data compression, takes place. Entropy coding involves the arranging the image components in a "zigzag" order, using run-length encoding (RLE) to group similar frequencies together.
How Not to be Read, a recipe using DCT:
- Choose a lofi JPEG base image on which macroblocking artifacts are slightly apparent. This JPEG will serve as the image on which your will write your secret message.
- If necessary, you can scale the image up via nearest neighbour interpolation, to preserve hard macroblock edges of the base image.
- Download and install the DCT font
- Position your secret message on top of the JPEG. Make sure the font has the same size as the macroblock artifacts in the image
- Flatten the layers (image and font) back to a JPEG. This will make the text no longer selectable and readable as copy and paste data.
︎ for the #3D Additivist Cookbook.
︎ DCT won the Crypto Desgin Challenge Award in 2015.
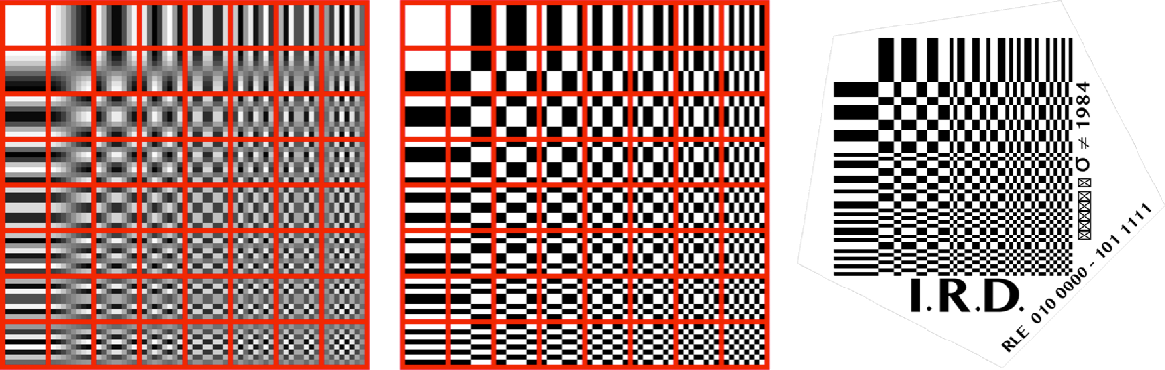
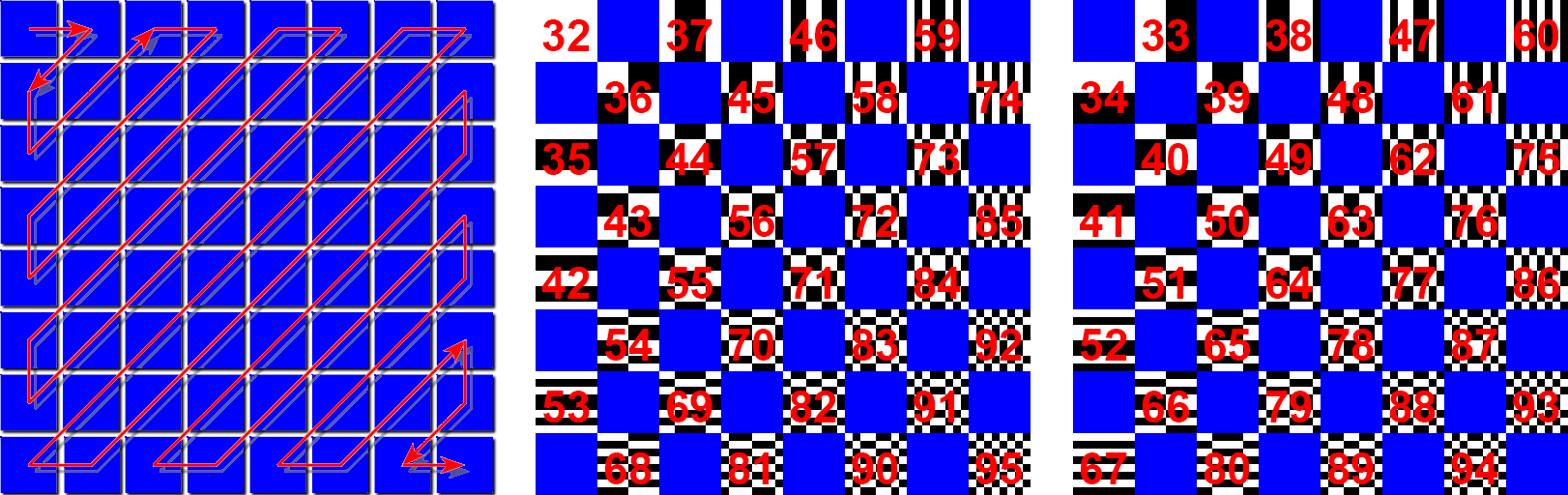 A Discrete Cosine Transform simplified to make a monochrome .ttf font and iRD logo. In the logo RLE 010 000 - 101 1111 signifies the key to the DCT encryption: 010 000 - 101 1111 are the binary values of the 64 most used ASCII glyphs, which are then mapped onto the DCT in a zig zag order (following RLE).
A Discrete Cosine Transform simplified to make a monochrome .ttf font and iRD logo. In the logo RLE 010 000 - 101 1111 signifies the key to the DCT encryption: 010 000 - 101 1111 are the binary values of the 64 most used ASCII glyphs, which are then mapped onto the DCT in a zig zag order (following RLE).

Discrete Cosine Transform (DCT) was first conceived for the Crypto Design Challenge
“A recipe using DCT” was released in the #Additivism cookbook.
Mesmerized by the screen, focusing on the moves of a next superhero, I was conditioned to ignore the dust imprinted on the celluloid or floating around in the theater, touching the light of the projection and mingling itself with the movie.
The dust – micro-universes of plant, human and animal fibers, particles of burnt meteorites, volcanic ashes, and soil from the desert – could have told me stories reaching beyond my imagination, deeper and more complex than what resolved in front of me, reflecting from the movie screen.
… But I never paid attention.
I focused my attention to where I was conditioned to look: to the feature, reflecting from the screen. All I saw were the images. I did not see the physical qualities of the light nor the materials making up its resolution; before, behind, and beyond the screen.
Decennia of conditioning the user to ignore these visual artifacts and to pay attention only to the overall image has changed these artifacts into the ultimate camouflage for secret messaging. Keeping this in mind, I developed DCT.
☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰
Premise of DCT is the realisation that the legibility of an encrypted message does not just depend on the complexity of the encryption algorithm, but also on the placement of the message. This encrypted message, hidden on the surface of the image, is only legible by the ones in the know; anyone else will ignore it. Like dust on celluloid, DCT is mimics JPEG error. It appropriates the algorithmic aesthetics of JPEG macroblocks to stenographically mask a secret message, mimicking error. The encrypted message, hidden on the surface of the image, is only legible by the ones in the know.
“A recipe using DCT” was released in the #Additivism cookbook.
Mesmerized by the screen, focusing on the moves of a next superhero, I was conditioned to ignore the dust imprinted on the celluloid or floating around in the theater, touching the light of the projection and mingling itself with the movie.
The dust – micro-universes of plant, human and animal fibers, particles of burnt meteorites, volcanic ashes, and soil from the desert – could have told me stories reaching beyond my imagination, deeper and more complex than what resolved in front of me, reflecting from the movie screen.
… But I never paid attention.
I focused my attention to where I was conditioned to look: to the feature, reflecting from the screen. All I saw were the images. I did not see the physical qualities of the light nor the materials making up its resolution; before, behind, and beyond the screen.
Decennia of conditioning the user to ignore these visual artifacts and to pay attention only to the overall image has changed these artifacts into the ultimate camouflage for secret messaging. Keeping this in mind, I developed DCT.
☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰☰
Premise of DCT is the realisation that the legibility of an encrypted message does not just depend on the complexity of the encryption algorithm, but also on the placement of the message. This encrypted message, hidden on the surface of the image, is only legible by the ones in the know; anyone else will ignore it. Like dust on celluloid, DCT is mimics JPEG error. It appropriates the algorithmic aesthetics of JPEG macroblocks to stenographically mask a secret message, mimicking error. The encrypted message, hidden on the surface of the image, is only legible by the ones in the know.







Making the Sun write cryptographic shadow messages wit DCT.

DCT at MOTI for the Crypto design challenge
Encrypted text:
The legibility of an encrypted message does not just depend on the complexity of the encryption algorithm, but also on the placement of the data of the message.
The Discreet Cosine Transform is a mathematical technique. In the case of the JPEG compression, a DCT is used to describe a finite set of patterns, called macroblocks, that could be described as the 64 character making up the JPEG image, adding lumo and chroma values as ‘intonation’.
If an image is compressed correctly, its macroblocks become ‘invisible’. The incidental trace of the macroblocks is generally ignored as artifact or error.
Keeping this in mind, I developed DCT. DCT uses the esthetics of JPEG macroblocks to mask its secret message as error. The encrypted message, hidden on the surface of the image is only legible by the ones in the know.
︎ A PDF about this work is downloadable here
︎ Visit the DCT ENCRYPTION STATION (2022, w/ Ted Davis) here
︎ DCT DECOY with Erik Axel Eggelink.
Encrypted text:
The legibility of an encrypted message does not just depend on the complexity of the encryption algorithm, but also on the placement of the data of the message.
The Discreet Cosine Transform is a mathematical technique. In the case of the JPEG compression, a DCT is used to describe a finite set of patterns, called macroblocks, that could be described as the 64 character making up the JPEG image, adding lumo and chroma values as ‘intonation’.
If an image is compressed correctly, its macroblocks become ‘invisible’. The incidental trace of the macroblocks is generally ignored as artifact or error.
Keeping this in mind, I developed DCT. DCT uses the esthetics of JPEG macroblocks to mask its secret message as error. The encrypted message, hidden on the surface of the image is only legible by the ones in the know.
︎ A PDF about this work is downloadable here
︎ Visit the DCT ENCRYPTION STATION (2022, w/ Ted Davis) here
︎ DCT DECOY with Erik Axel Eggelink.